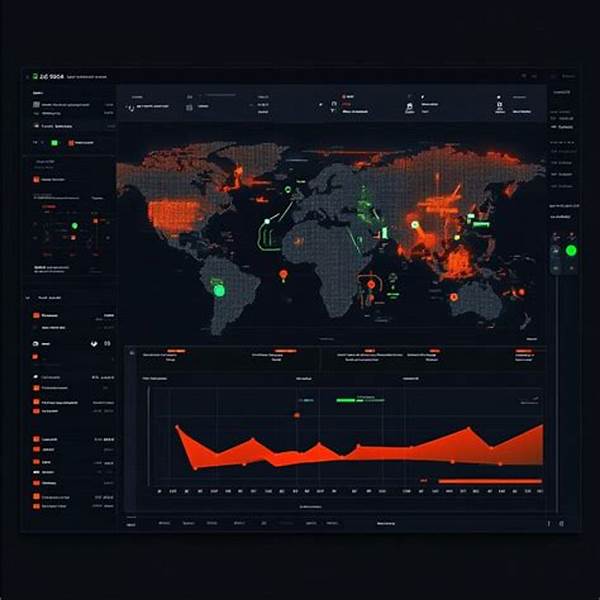
In an era where cybersecurity threats are constantly evolving, organizations require advanced solutions to protect their digital assets. One such solution is real-time threat analytics customization, allowing businesses to tailor their threat detection systems to address specific security needs. This approach enhances the ability to identify, analyze, and respond to threats promptly, ensuring robust security measures are in place.
Read Now : Durable Battery Bluetooth Headset
Benefits of Real-Time Threat Analytics Customization
Real-time threat analytics customization offers numerous advantages to organizations aiming to bolster their cybersecurity posture. Firstly, it allows for a tailored approach to threat detection. By customizing the analytics, businesses can focus on specific threats relevant to their operations. This ensures that resources are efficiently allocated towards addressing the most significant vulnerabilities.
Secondly, customization enhances the speed and accuracy of threat detection. With real-time analytics, organizations can swiftly identify unusual patterns or activities within their network. The customized setup enables rapid responses, effectively mitigating potential damages before they escalate. Lastly, real-time threat analytics customization promotes proactive security measures. By continuously monitoring and adjusting the system to evolving threats, companies remain one step ahead in safeguarding their data and infrastructure.
Beyond merely reacting to threats, this approach fosters a culture of continuous improvement in cybersecurity practices. Organizations can regularly assess their threat analytics setup and adjust it to align with emerging security trends and potential risks. Ultimately, real-time threat analytics customization empowers businesses to maintain a resilient defense against ever-evolving cyber threats.
Key Elements of Real-Time Threat Analytics Customization
1. Targeted Threat Detection: Real-time threat analytics customization enables businesses to direct their efforts towards specific threats pertinent to their industry, enhancing defense capabilities.
2. Enhanced Response Time: A customized analytics setup drastically reduces the time taken to detect and respond to threats, allowing for immediate countermeasures.
3. Improved Accuracy: Tailoring analytics ensures that the detection systems have higher accuracy in identifying genuine threats, minimizing false positives.
4. Cost Efficiency: By concentrating resources on the most pertinent threats, real-time threat analytics customization optimizes security expenditure and resource allocation.
5. Proactive Security Approach: This customization encourages regular updates to the analytics frameworks, ensuring preparedness for emerging threats and maintaining robust security.
Strategies for Implementing Real-Time Threat Analytics Customization
To effectively implement real-time threat analytics customization, organizations must adopt strategic measures. One crucial strategy is to align analytics customization with business objectives. By understanding the specific threats that impact their operations, companies can tailor their threat analytics to address those vulnerabilities directly. This strategic alignment optimizes resource allocation and strengthens threat detection capabilities.
Furthermore, incorporating machine learning and artificial intelligence into analytics customization can enhance threat prediction and response. These technologies provide adaptive learning, enabling the system to quickly adjust to evolving threats. By leveraging AI-driven insights, businesses can anticipate potential security breaches, allowing for swift preventive actions. This proactive stance minimizes risk and shields valuable data from harm.
Lastly, fostering a culture of collaboration among security teams is vital. By sharing insights and experiences, organizations can refine their analytics customization. This collaborative approach ensures that real-time threat analytics customization evolves in parallel with emerging cybersecurity challenges, maintaining robust protection across the organization.
Read Now : Swift Machine Learning Toolkit Examples
Challenges in Real-Time Threat Analytics Customization
Implementing real-time threat analytics customization presents several challenges. First, organizations must overcome the complexity of integrating customized solutions into existing systems. This often requires specialized expertise and a substantial investment in time and resources to ensure seamless integration.
Second, data privacy concerns can arise when customizing analytics systems, as they often involve monitoring vast quantities of sensitive information. Organizations need to establish strict data protection policies to prevent unauthorized access and ensure compliance with regulatory standards. Lastly, the constantly changing threat landscape demands continuous adjustment of analytics systems. Organizations must remain vigilant and adapt swiftly to new threats to maintain the effectiveness of their customized analytics solutions.
The Future of Real-Time Threat Analytics Customization
As cyber threats continue to grow in sophistication, the future of real-time threat analytics customization lies in harnessing advanced technologies. Organizations are likely to see increased integration of AI and machine learning, providing more refined and automated threat detection capabilities. These technologies offer immense potential to predict and counteract threats with unprecedented precision.
Moreover, the shift towards greater organizational collaboration in cybersecurity will be pivotal. By fostering environments where information and threat intelligence are shared among different entities, businesses can enhance their analytic customization practices. This collaborative approach will enable more comprehensive threat mitigation strategies, providing a robust defense against increasingly complex cyber threats.
Ultimately, real-time threat analytics customization will evolve into a fundamental component of cybersecurity frameworks. As the digital landscape becomes more intricate and interconnected, advanced real-time analytics capabilities will be essential for safeguarding organizational assets and maintaining operational integrity.
Key Considerations for Effective Customization
Success in real-time threat analytics customization demands attention to key considerations. Firstly, organizations must prioritize the identification of critical assets and vulnerabilities to focus their customization efforts. This ensures the most vital areas receive the necessary protection. Additionally, maintaining an agile approach is crucial. By regularly evaluating and updating analytical frameworks, businesses can adapt to new threats efficiently.
Collaboration between IT and security teams is another crucial factor. Effective communication ensures entities are aligned in their customization strategies and can respond cohesively to threats. Finally, investing in continued education and training for staff aids in maintaining a knowledgeable workforce, capable of comprehending and implementing the latest advancements in threat analytics customization.
Summary
In summary, real-time threat analytics customization is an indispensable tool for modern organizations looking to reinforce their cybersecurity postures. By tailoring threat detection systems to address specific security needs, companies can prioritize and mitigate risks more effectively. Real-time threat analytics customization significantly reduces the time taken to identify and neutralize threats, minimizing potential damage.
The implementation, however, requires a concerted effort, involving careful planning and integration into existing infrastructures. Organizations need to balance the complexity of customization with robust data privacy measures, while continuously refining their analytics in response to emerging threats. With the evolving digital ecosystem, the strategic use of advanced technologies like AI promises to further enhance customization capabilities. Ultimately, real-time threat analytics customization will play a vital role in the ongoing battle against cyber threats, empowering organizations to protect their digital assets with greater precision and efficacy.