The digital age brings unparalleled convenience but also unprecedented risks. Among these risks, malware stands out as a formidable adversary that threatens the integrity, confidentiality, and availability of data. To combat these threats, experts are increasingly turning to algorithmic approaches to malware detection. These approaches leverage complex algorithms, machine learning, and artificial intelligence to identify and neutralize malicious software before it wreaks havoc on systems. The appeal of such solutions lies in their potential to adapt and evolve, staying one step ahead of cybercriminals.
Read Now : How To Fix Computer Freezing Problems
Understanding Algorithmic Approaches
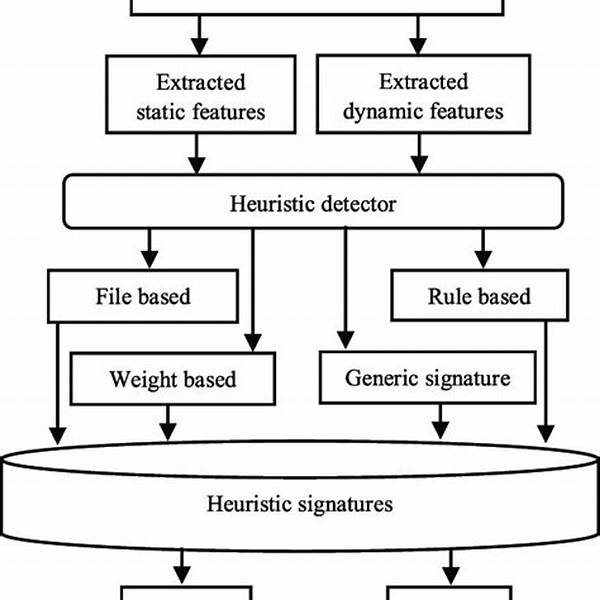
Algorithmic approaches to malware detection encompass a variety of techniques, each with its unique strengths. One popular method involves signature-based detection, where unique patterns or digital fingerprints of known malware samples are identified. However, the rapid evolution of malware can render this technique less effective. This is why heuristic and behavior-based methods are increasingly favored. These strategies identify unusual activities or processes that signal potential threats, allowing systems to catch previously unknown malware types. Machine learning algorithms also play a vital role. By analyzing vast datasets, these algorithms can predict potential threats and learn to recognize new malware variants without explicit programming.
Another exciting frontier in algorithmic approaches to malware detection is the use of deep learning. These advanced neural networks can autonomously identify intricate patterns and correlations in large datasets, improving detection rates and reducing false positives. The adaptability and continuous learning capabilities inherent in these systems make them formidable tools against a constantly evolving malware landscape. As cyber threats become more sophisticated, these algorithmic solutions provide a promising avenue to enhance cybersecurity defenses.
Techniques in Algorithmic Detection
1. Signature-Based Detection: Part of algorithmic approaches to malware detection is using known patterns of malware. While efficient, it is limited to known threats.
2. Heuristic Analysis: This involves examining the behavior of files and programs. It is a crucial component of algorithmic approaches to malware detection for catching new threats.
3. Machine Learning Integration: Algorithmic approaches to malware detection are significantly enhanced by machine learning, allowing systems to learn from data and predict threats.
4. Behavioral Analysis: Observing ongoing processes, this tactic in algorithmic approaches to malware detection identifies anomalies in real-time.
5. Deep Learning Techniques: These offer immense potential in algorithmic approaches to malware detection by recognizing complex patterns, continually evolving to counteract emerging malware.
Advantages of Algorithmic Methods
The primary advantage of algorithmic approaches to malware detection lies in their adaptability and learning capabilities. Unlike traditional methods reliant on static databases, algorithmic solutions evolve with the cyber threat landscape. This dynamic nature ensures up-to-date protection against new and unknown malware variants. Furthermore, these techniques provide a higher accuracy rate. By analyzing behavior and leveraging machine learning, they minimize false positives, offering more reliable security measures. Scalability is another critical benefit, as algorithmic methods can be deployed across various platforms and scales, providing comprehensive security coverage.
Moreover, algorithmic approaches often facilitate faster detection and response times. With threats being identified and neutralized in real-time, systems experience minimal downtime and reduced risk of data breaches. As organizations continue to amass vast amounts of data, the capacity of algorithmic solutions to process and analyze this data more efficiently becomes increasingly invaluable. In an era of ever-evolving threats, these advancements represent a proactive step towards robust cybersecurity.
The Challenge of False Positives
Despite the many advancements, algorithmic approaches to malware detection are not without their challenges. One significant issue is the potential for false positives—flagging legitimate software or processes as threats, which can disrupt business operations. Fine-tuning these algorithms to balance sensitivity and specificity is a continuous challenge. Addressing this involves continuous training with diverse datasets to improve accuracy. Testing these algorithms in varied and dynamic environments is crucial to minimize disruptions caused by erroneous detections.
Read Now : Multi-adjustable Armrests For Comfort
Ensuring the efficacy of algorithmic approaches to malware detection also demands integration with existing cybersecurity protocols. Collaborations between experts in machine learning, network security, and system administrators can create more robust solutions. Sharing threat intelligence across industries further enhances the development of effective algorithmic defenses. As cybercriminals employ increasingly sophisticated methods, the collaboration and constant evolution of these approaches remain vital in maintaining a strong defense posture.
Transforming Cybersecurity Strategies
As we delve deeper into the digital age, the imperative to continuously improve and refine our cybersecurity strategies becomes more pressing. Algorithmic approaches to malware detection hold the key to revolutionizing how organizations protect themselves against cyber threats. The potential of these algorithms to analyze and predict malicious activities transforms them from reactive to proactive tools. They not only identify threats but also predict and forestall future attacks. The seamless integration of these technologies into existing security frameworks offers considerable opportunities for enhanced security operations.
As more industries adopt these advanced methods, scaling the deployment of algorithmic solutions becomes paramount. It is essential to create flexible frameworks capable of adapting to the unique needs of different sectors. Additionally, fostering a culture of continuous learning and improvement will ensure that security measures evolve in tandem with emerging threats. The future of cybersecurity lies in the embracing of advanced technologies and a commitment to innovation, enabling a safer and more secure digital landscape.
Continuous Evolution and Innovation
One of the hallmarks of algorithmic approaches to malware detection is their continuous evolution. By advancing machine learning models and incorporating novel technologies, these methods steadily improve in accuracy and reliability. Staying ahead of malicious actors requires an unyielding commitment to innovation, ensuring defenses remain capable of thwarting evolving threats. Regular updates and training of algorithms with diverse data enable systems to recognize a broader range of threats, providing a proactive defense mechanism.
Moreover, fostering collaboration between researchers, cybersecurity experts, and developers is crucial. It encourages the exchange of ideas and insights, ultimately leading to the development of more sophisticated defenses. Organizations investing in these collaborative efforts gain access to shared knowledge, allowing them to implement comprehensive security solutions tailored to specific needs. As technology progresses, so too must the approaches we take to protect ourselves from the ever-present threat of malware.
Future Prospects of Cybersecurity
The future of cybersecurity is inherently tied to the advancement of intelligent systems capable of predictive modeling and autonomous threat response. Algorithmic approaches to malware detection pave the way for these future technologies, setting the foundation for more interactive and intuitive security measures. By prioritizing adaptability, machine intelligence, and real-time processing, these solutions will become integral in safeguarding digital infrastructures globally. As we progress, the seamless integration of AI-driven technologies will allow for more streamlined and efficient responses to threats, significantly bolstering overall security posture.
Organizations must remain vigilant and forward-thinking in their adoption of these advanced methods, ensuring they stay resilient against the dynamic and complex nature of digital threats. Through ongoing research, development, and collaboration, the cybersecurity landscape will continue to evolve, resulting in robust defense mechanisms faithful to the ever-changing necessities of the digital era. The commitment to innovation and adaptability is essential, ensuring a secure future in which digital connectivity can thrive without compromise.