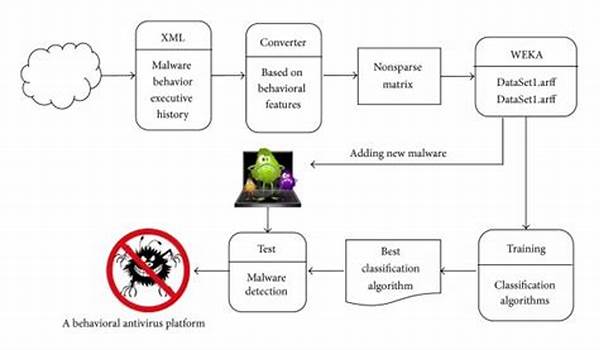
In today’s digitally-driven world, cybersecurity is more critical than ever. With increasing threats lurking in cyberspace, defending against malware has become a significant concern for businesses and individuals alike. One cutting-edge approach to combating these threats is behavior-based malware classification.
Read Now : Feature-rich Webcam Streaming Tools
Understanding Behavior-Based Malware Classification
Behavior-based malware classification is a method that focuses on monitoring and analyzing the actions of potentially malicious software to determine its threat level. Unlike traditional signature-based detection that relies on known malware signatures, behavior-based techniques observe how the software behaves within a system. By identifying abnormal or suspect actions, this method provides an extra layer of protection against previously unknown threats.
This technique is particularly effective because it does not rely solely on existing malware databases. Instead, it watches how a piece of software interacts with the host system’s environment. For example, if a program attempts to access sensitive files repeatedly or changes system settings without consent, these behaviors can raise red flags. Behavior-based malware classification is a dynamic approach that adapts to new malware strains that exhibit novel behaviors, making it a vital tool in modern cybersecurity arsenals.
With malware becoming more sophisticated, behavior-based malware classification serves as a proactive defense mechanism. It enables cybersecurity systems to preemptively address potential threats, even those that have yet to be documented. As part of a larger defense strategy, this classification method can significantly reduce the chances of security breaches, ensuring safer digital environments for users.
Advantages of Behavior-Based Malware Classification
1. Real-time Threat Detection: Behavior-based malware classification offers real-time insights into potential threats by monitoring software activity, thus enhancing immediate response strategies.
2. Adaptability to New Threats: As cyber threats evolve, behavior-based malware classification remains effective by identifying novel behaviors, not just known signatures.
3. Reduction in False Positives: By analyzing behavior, this method helps reduce false positive rates compared to traditional methods, providing more accurate threat assessments.
4. Layered Security Approach: Behavior-based classification complements traditional methods, offering a layered security strategy that enhances overall system protection.
5. Autonomous Learning: The classification system improves over time through autonomous learning mechanisms, continuously enhancing its detection capabilities.
Implementing Behavior-Based Malware Classification
Incorporating behavior-based malware classification into existing security frameworks requires a strategic approach. Organizations must first assess their current security posture and identify gaps where behavior-based techniques can add value. Integrating these advanced techniques with traditional methods, such as signature-based detection, enhances the overall security infrastructure.
Training is an essential component of implementation. Staff should be educated on the significance of behavior-based malware classification and trained to interpret its findings. This understanding ensures that the human element in security is as robust as the technology itself, fostering a culture of cybersecurity awareness within the organization.
Organizations might also consider investing in advanced tools and technologies that support behavior-based malware classification. Many modern endpoint security solutions come equipped with built-in behavior analysis capabilities, offering seamless integration and enhanced protection. By choosing solutions that provide regular updates and support, companies can maintain their defenses against evolving threats effectively.
Challenges in Behavior-Based Malware Classification
Despite its advantages, behavior-based malware classification faces several hurdles. One major challenge is distinguishing between legitimate software behavior and actual malicious activity. This distinction requires sophisticated algorithms and constant refinement of detection parameters to minimize errors.
Another challenge is the potential computational overhead. Monitoring and analyzing behavior in real-time can be resource-intensive, requiring robust infrastructure to avoid performance bottlenecks. Balancing security concerns with system efficiency remains a priority for organizations employing this technique.
Read Now : Affordable Graphics Card Recommendations
Behavior-based malware classification also demands regular system updates and rule-set refinements. As new malware behaviors emerge, classification systems need to adjust accordingly to maintain their efficacy. This continual updating process requires a commitment to ongoing research and development, presenting another layer of operational complexity.
Enhancing Detection with Behavior-Based Malware Classification
Optimizing behavior-based malware classification involves leveraging artificial intelligence and machine learning techniques. These technologies provide the computational power and sophistication needed to process large volumes of behavioral data accurately. Employing advanced algorithms, AI-related tools can discern patterns that human analysts may overlook.
Machine learning enhances the autonomy of behavior-based systems. As they process more data, these systems learn to improve their threat recognition capabilities continually. By automating repetitive tasks and analyses, machine learning frees security personnel to focus on strategic threat assessment and remediation.
By integrating AI and machine learning with behavior-based malware classification, organizations can maintain a proactive security stance. This integration ensures that defenses evolve alongside emerging threats, maintaining a robust shield against potential security breaches. As the cyber threat landscape continues to evolve, staying ahead with advanced analytical capabilities becomes not just advantageous but necessary.
The Future of Behavior-Based Malware Classification
The horizon of behavior-based malware classification is promising. With continuous advancements in AI and machine learning, the accuracy and effectiveness of behavior-based techniques are set to improve further. Organizations can expect these methods to become cornerstones of comprehensive cybersecurity strategies.
As cyber threats grow in complexity and frequency, adaptive defense mechanisms like behavior-based malware classification will be indispensable. Embracing these technologies promises not only enhanced security but also a competitive edge in safeguarding digital assets. Ignoring such advances might mean inviting unnecessary risks.
Collaboration between tech companies and cybersecurity researchers will drive the evolution of behavior-based malware classification. By pooling knowledge and resources, the industry can develop standardized protocols and best practices that can be adopted widely, ensuring safer cyber environments for all.
Summary: The Value of Behavior-Based Malware Classification
In summary, behavior-based malware classification represents a crucial evolution in the fight against cyber threats. This approach stands out for its ability to detect previously unseen malware by observing anomalies in software behavior. By emphasizing real-time threat detection and adaptability, it fills the gaps left by traditional methods.
Organizations adopting behavior-based malware classification enjoy enhanced protection capabilities. The inclusion of AI and machine learning in this approach significantly boosts its effectiveness, offering a proactive defense against cyber threats. This proactive stance not only reduces risks but also allows organizations to stay ahead of malicious actors.
As the digital landscape continues to evolve, the importance of robust cybersecurity can’t be overstated. Behavior-based malware classification, with its innovations and enhancements, exemplifies the next frontier in digital defense strategies. Embracing this method ensures that organizations remain resilient in the face of ever-growing cyber challenges.