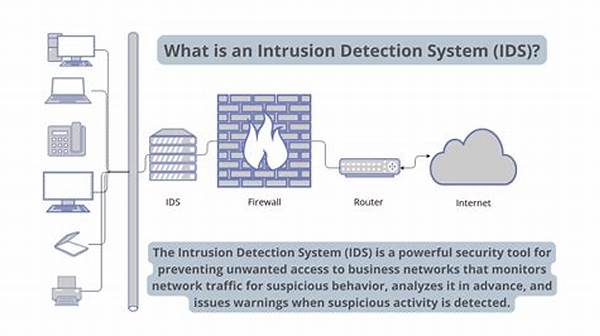
In today’s rapidly evolving digital landscape, the importance of cybersecurity cannot be overstated. One fundamental component of a comprehensive security strategy is an effective Intrusion Detection System (IDS). The primary role of an IDS is to monitor network traffic for suspicious activity and alert organizations to potential threats. This article will explore various intrusion detection system techniques, offering insights into their functionality and effectiveness.
Read Now : Economical Gaming Graphics Units
Understanding Intrusion Detection System Techniques
Intrusion detection system techniques form the backbone of detecting unauthorized access or anomalies within a network. These techniques are primarily categorized into signature-based detection, anomaly-based detection, and hybrid detection. Signature-based detection relies on identifying known patterns associated with malicious activity. This method is highly effective for recognizing previously encountered threats quickly. On the other hand, anomaly-based detection focuses on identifying deviations from normal network behavior. This technique is crucial for detecting new or unknown threats that do not match any known signatures. Hybrid detection, as the name suggests, combines elements of both signature and anomaly-based techniques. By leveraging the strengths of both approaches, hybrid detection can provide a more comprehensive security solution, capable of identifying both known and novel threats. The continuous development and refinement of these intrusion detection system techniques play a critical role in building robust network defenses.
Key Intrusion Detection System Techniques Explained
1. Signature-Based Detection: This technique uses predefined signatures of known threats to identify intrusions. While effective against known attacks, it may struggle with zero-day threats where no signature exists.
2. Anomaly-Based Detection: By establishing a baseline of normal network behavior, this technique identifies deviations that may indicate an attack. It’s useful for spotting unknown threats but can yield false positives.
3. Hybrid Detection: Combining signature and anomaly-based methods, hybrid detection systems aim to provide more balanced security coverage. They offer improved detection capabilities but may require significant resources.
4. Host-Based Detection: This technique involves monitoring activity on individual devices or hosts within a network. It’s critical for detecting internal threats but may not cover network-wide anomalies thoroughly.
5. Network-Based Detection: By analyzing traffic across a network, this technique can identify widespread threats and suspicious activity. However, it may not detect threats confined to a single host.
Advancements in Intrusion Detection System Techniques
With the ever-increasing complexity of cyber threats, intrusion detection system techniques continue to evolve. Recent advancements in artificial intelligence and machine learning have introduced more dynamic and adaptive detection capabilities. Machine learning algorithms can analyze patterns and behaviors over time, learning what constitutes normal activity to better detect anomalies. These intelligent systems are continually improving, adapting to changes in network environments and evolving threat landscapes. Additionally, the integration of data analytics has enhanced the efficiency and accuracy of intrusion detection system techniques. By leveraging vast amounts of data, these systems can identify subtle patterns and improve threat detection rates. As technology advances, so too does the sophistication with which we can protect our networks against unauthorized access and cyber threats.
Specialized Intrusion Detection System Techniques
1. Behavioral Analysis: This technique examines user actions and compares them against expected behavior patterns, aiding in the detection of insider threats and compromised accounts.
2. Protocol Analysis: By studying the protocols used for communication, this technique can identify anomalies indicative of an intrusion attempt or attack vector.
3. Deception Technology: Creating decoy resources within a network, this technique can lure and trap attackers while alerting security teams to their presence.
4. Heuristic-Based Detection: Employing heuristics, this method evaluates the likelihood of activities being malicious, often used alongside other techniques to enhance detection.
Read Now : Remote Color Changing Led
5. Correlation Analysis: This approach links disparate security events to identify complex attack patterns, improving detection of sophisticated cyber-attacks.
6. Statistical Analysis: Utilizing statistics, this method establishes thresholds and patterns to discern normal from potentially harmful behaviors.
7. Reputation-Based Detection: Leveraging information about known malicious entities, this technique assesses the credibility of various network activities and interactions.
8. Hybrid Deception Techniques: Combining traditional detection with deception strategies, this approach enhances the ability to detect, engage, and understand attackers.
9. Automated Threat Hunting: Advanced systems can automatically search for potential threats by continuously analyzing data to detect suspicious activities without human intervention.
10. Collaborative Defense Systems: By sharing threat intelligence across multiple organizations, this technique helps in building robust and preemptive defense strategies.
Future Prospects of Intrusion Detection System Techniques
The future of intrusion detection system techniques is promising, with emerging technologies paving the way for more robust and intelligent solutions. As cyber threats become increasingly sophisticated, the integration of artificial intelligence (AI) and machine learning (ML) into IDS technologies is crucial. These systems are evolving to not only detect potential breaches but also predict and prevent them. Predictive analytics allow organizations to anticipate threats before they occur, significantly enhancing security postures. Furthermore, the rise of decentralized networks and the Internet of Things (IoT) presents unique challenges, requiring intrusion detection systems to become more adaptable and scalable. Continued research and innovation will lead to the development of more comprehensive intrusion detection system techniques that support these advancements. As organizations strive to stay ahead of cyber threats, the ongoing evolution of IDS technologies will be instrumental in safeguarding digital ecosystems.
The Necessity for Continuous Adaptation
In the realm of cybersecurity, intrusion detection system techniques must continuously adapt to remain effective against an ever-evolving threat landscape. The dynamic nature of cyber threats means that yesterday’s solutions may not withstand today’s challenges. Therefore, ongoing research and development, combined with a willingness to adopt innovative approaches, are crucial for maintaining robust security postures. Organizations need to stay informed about the latest advancements in IDS technologies to ensure their networks are protected against both known and emerging threats. Intrusion detection system techniques are not just about immediate threat detection; they are a fundamental part of risk management and strategic planning for future security. By understanding and implementing these cutting-edge techniques, organizations can better shield themselves from potential cyber-attacks, protecting both their data and reputation from harm. As technology advances, so too will the capabilities of IDS, driving the continuous evolution needed to meet tomorrow’s security demands.