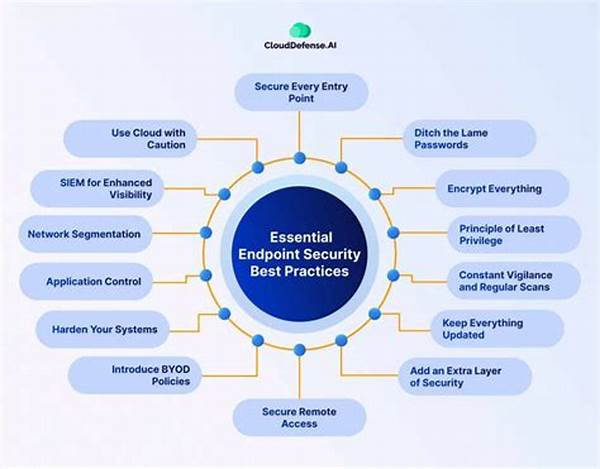
In the ever-evolving landscape of cyber threats, businesses must prioritize safeguarding their digital assets, with comprehensive endpoint security software playing a pivotal role. This type of security solution not only protects devices from external threats but also ensures that sensitive data remains intact and accessible only to authorized personnel. As the complexity of threats rises, having a robust security measure in place becomes indispensable. It’s essential to understand the capabilities and benefits that comprehensive endpoint security software can offer. This discussion delves into various aspects and advantages of employing such software in a business environment.
Read Now : Software For Managing Gaming Focus
Understanding the Essence of Comprehensive Endpoint Security Software
Comprehensive endpoint security software serves as a robust shield for network devices, ranging from laptops and desktops to mobile gadgets. It safeguards endpoints by preventing unauthorized access, detecting potential threats, and responding to incidents swiftly. With the rise of remote work, the number of endpoints within an organization has increased, making the deployment of reliable security software crucial. An effective endpoint security solution can defend against malware, phishing attacks, and data breaches, protecting sensitive company information from cybercriminals. By integrating advanced technologies such as machine learning and behavioral analysis, comprehensive endpoint security software ensures an adaptive defense mechanism. Businesses leveraging these solutions can maintain operational integrity, prevent financial losses, and sustain their reputation by averting security incidents. Thus, adopting a comprehensive endpoint security strategy is no longer a luxury but a necessity for contemporary organizations.
Key Features of Comprehensive Endpoint Security Software
1. Unified Threat Management
Comprehensive endpoint security software consolidates multiple security functions, offering streamlined protection across various devices.
2. Real-time Threat Intelligence
This software equips organizations with up-to-date threat data, ensuring preemptive defense against emerging cyber threats.
3. Scalability and Flexibility
Designed to adjust to the unique needs of various businesses, comprehensive endpoint security software supports seamless scaling.
4. User-friendly Interface
With an intuitive design, comprehensive endpoint security software enhances user experience while simplifying management tasks.
Read Now : Real-time Voice Transmission Methods
5. Automated Incident Response
Comprehensive endpoint security software incorporates automation to rapidly address security incidents, minimizing potential damage.
Benefits of Comprehensive Endpoint Security Software
Comprehensive endpoint security software offers a multi-layered defense strategy to shield network infrastructures from diverse cyber threats. This sophisticated software employs a combination of detection techniques, including signature-based and behavioral analysis, to ensure proactive protection. By continuously monitoring network activities, the software can swiftly detect anomalies, curbing potential threats before they escalate into significant problems. Furthermore, comprehensive endpoint security software facilitates efficient policy management and compliance with industry regulations. By enforcing stringent security measures, businesses can mitigate risks and enhance their credibility in the marketplace. Beyond protection, this software also optimizes IT resources by minimizing manual intervention through automation, enabling IT teams to focus on strategic initiatives. All these benefits culminate in fortifying business operations, ensuring that companies can thrive securely in the digital age.
Importance of Comprehensive Endpoint Security Software
Choosing the Right Comprehensive Endpoint Security Software
When selecting comprehensive endpoint security software, businesses must consider factors like scalability, integration capabilities, and ease of management. A software solution should effortlessly integrate with existing infrastructure to provide seamless protection. It’s crucial to evaluate the software’s ability to evolve with technological advancements and emerging cyber threats. Cost-effectiveness is another critical aspect, ensuring that the software provides value without compromising on essential features. Businesses should also focus on vendor reliability, ensuring that the chosen provider offers robust support and continuous updates. With the effectiveness of a comprehensive endpoint security strategy hinging on various aspects, making the right choice can substantially enhance a business’s defense against cyber threats. Moreover, user feedback and industry reviews can provide valuable insights into the practical performance and reliability of a security solution. In conclusion, a well-chosen comprehensive endpoint security software can significantly contribute to safeguarding business operations, leading to sustained growth and success in a challenging digital environment.
Detailed Overview of Comprehensive Endpoint Security Software
Selecting the appropriate comprehensive endpoint security software necessitates a deep understanding of the organizational needs and threat landscape. This security solution must integrate advanced threat detection features, including heuristic and AI-powered tools, to combat sophisticated cyber threats. Regular updates and a resilient support structure are imperative to ensure that the software remains effective against newly emerging vulnerabilities. Another focus point for businesses should be ensuring robust vendor support, an aspect critical for seamless software deployment and troubleshooting. The software should ideally be intuitive, allowing easy administration while offering transparent reporting functions. These functions can provide insights into potential threats and trends, guiding the organization’s security strategy. Finally, a comprehensive endpoint security software not only protects but also enhances productivity by allowing businesses to concentrate on primary objectives while security functions are efficiently managed in the background. Consequently, implementing a well-rounded endpoint security software ensures that organizations can effectively safeguard their digital assets and continue their operations with peace of mind.
Summary and Final Thoughts
In conclusion, comprehensive endpoint security software is essential for modern businesses aiming to maintain robust cyber protections. By combining multiple security layers, this software defends against various threats, from malware to data breaches. Its ability to adapt and learn from new threats is especially crucial in today’s dynamic digital landscape. Selecting such software involves careful consideration and understanding of the specific needs of your organization, ensuring that it fits seamlessly into existing systems and scales as needed. Additionally, support from the software vendor can make a significant difference in the ongoing effectiveness and usability of the security solution. Ultimately, comprehensive endpoint security software is not just about defense but also about sustaining operational efficiency and trust. In a world where cyber threats are increasingly sophisticated, investing in reliable endpoint security is a proactive step toward long-term resilience and success.