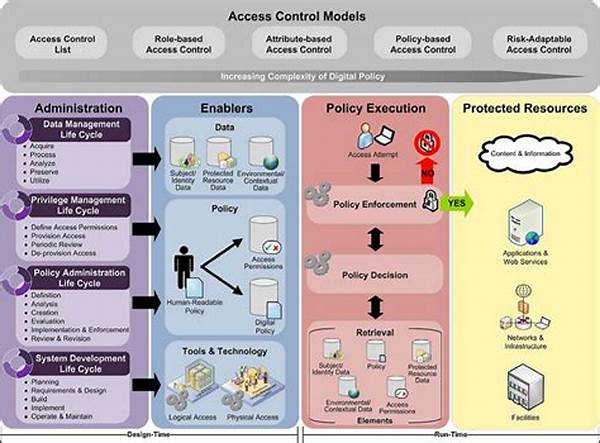
Access control policy frameworks serve as the backbone of organizational security, defining who is authorized to access certain resources and under what conditions. In today’s digital age, where data breaches are rampant, a robust access control policy framework is vital for safeguarding sensitive information. It allows organizations to regulate permissions and ensure that only authorized users can access specific data or systems. This balance between accessibility and security is crucial for both protecting assets and maintaining operational efficiency.
Read Now : Enhanced Realism In Gaming Controls
Understanding the Components of Access Control Policy Frameworks
An effective access control policy framework is composed of several key elements. At its core, the framework must delineate roles and responsibilities within an organization. This creates clarity and ensures that each user is granted appropriate access levels. Additionally, the framework must incorporate authentication mechanisms to verify users’ identities, thereby providing an extra layer of security. Another critical component is the continuous monitoring and auditing of access activities to detect any potential security breaches promptly.
Furthermore, flexibility is crucial in an access control policy framework. As businesses grow and evolve, access needs may change. Thus, the framework should be adaptable to accommodate new roles, technologies, and security challenges. An agile access control policy framework can effectively respond to emerging threats while keeping pace with organizational changes. This ability to adapt underscores the importance of regular reviews and updates to the framework, ensuring it remains aligned with current security standards.
Key Benefits of an Access Control Policy Framework
1. Enhanced Security: An access control policy framework fortifies an organization’s defenses by enforcing stringent access rules tailored to specific needs.
2. Compliance Assurance: Regulatory compliance is made more straightforward with an access control policy framework that aligns with industry standards.
3. Risk Management: By clearly defining access levels, organizations can minimize the risk of unauthorized access and data breaches.
4. Operational Efficiency: Streamlined access management allows for smooth operations without unnecessary delays caused by access issues.
5. Trust Building: Clients and stakeholders are likely to have increased trust in an organization that implements a robust access control policy framework.
Implementing an Effective Access Control Policy Framework
Implementing a comprehensive access control policy framework is not an overnight task. It requires a well-planned strategy, starting with an assessment of current security gaps. Organizations must tailor the framework to their specific needs, considering factors such as the nature of their data, regulatory requirements, and organizational structure. Collaboration among IT, security teams, and other stakeholders is essential in crafting a well-rounded policy.
The next step involves deploying technologies and tools to support the framework. This might include advanced identity and access management (IAM) systems that automate and streamline permission management. Training is also vital; employees must understand the importance of adhering to access control policies and recognize the role they play in maintaining security. Finally, regular audits and updates are necessary to ensure that the access control policy framework remains effective against evolving threats.
Challenges in Maintaining an Access Control Policy Framework
1. Scalability Issues: As organizations grow, maintaining a scalable access control policy framework can become complex, requiring dynamic adjustments.
2. User Compliance: Employees may not always comply with access control policies, necessitating ongoing training and reinforcement of best practices.
3. Technological Changes: Rapid technological advancements can render existing frameworks obsolete unless they are regularly updated.
4. Resource Limitations: Developing and maintaining a robust access control policy framework can be resource-intensive, demanding time and expertise.
Read Now : Disable Windows Visual Effects
5. Integration with Legacy Systems: Integrating new access controls with outdated systems can present significant challenges, potentially exposing security vulnerabilities.
6. Managing Role-Based Access: Defining and managing roles, especially in large enterprises, can be difficult due to overlapping responsibilities.
7. Balancing Security and Accessibility: Finding the right balance between security and ease of access for users is a constant challenge.
8. Data Privacy Considerations: An access control policy framework must also consider data privacy regulations, impacting design decisions.
9. Continuous Monitoring: Regular monitoring to identify policy violations or security breaches adds an additional layer of complexity.
10. Stakeholder Coordination: Ensuring all stakeholders are aligned in their understanding and implementation of the access control policy framework requires constant collaboration.
Conclusion and Future Outlook
The access control policy framework is indispensable in the modern technology landscape. As cyber threats become more sophisticated, the need for efficient and adaptive frameworks will continue to grow. Organizations must remain vigilant and proactive, ensuring their frameworks are capable of addressing new challenges.
By investing in the ongoing development and refinement of these frameworks, businesses can protect their assets and maintain trust with their clients. The future of access control lies in automation and machine learning, equipping systems to predict and respond to threats autonomously. Embracing these technologies will enable organizations to create more resilient and responsive access control policy frameworks that stand the test of time.
Summary of Access Control Policy Framework
In summary, the access control policy framework plays a pivotal role in securing an organization’s digital environment. It establishes clear guidelines for who can access which resources and under what conditions. This not only protects sensitive information but also ensures compliance with regulatory requirements, fostering a secure and efficient operational atmosphere.
The access control policy framework’s effectiveness largely hinges on its adaptability and precision. As threats evolve, so too must the strategies for managing access. By dedicating resources to regularly update and refine this framework, organizations can mitigate risks, improve compliance, and establish stronger security postures. The continuous evolution of access control strategies will be key to safeguarding organizational integrity in an increasingly interconnected world.