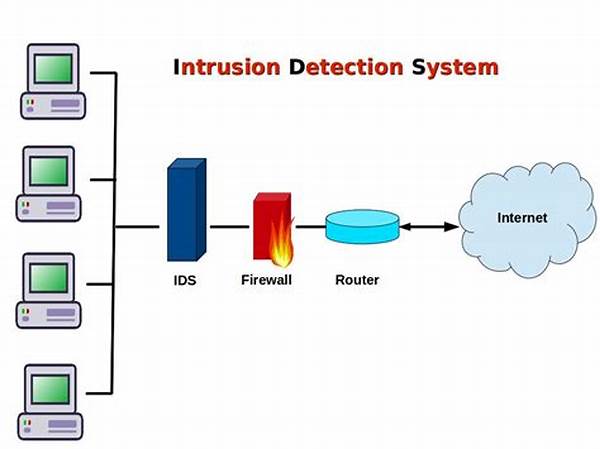
In the digital age, where data is the lifeline of most organizations, ensuring the security of network systems is paramount. As cyber threats become more sophisticated and varied, it becomes crucial for businesses and industries to implement robust defenses to safeguard their sensitive information. One of the most effective tools in the cybersecurity arsenal is the Network Intrusion Detection System (NIDS). These systems play a vital role in monitoring network traffic for suspicious activities and potential breaches, providing a layer of protection that is indispensable in today’s cyberspace landscape.
Read Now : Footrest Impact On Posture
Understanding Network Intrusion Detection Systems
Network intrusion detection systems are specialized devices or software applications designed to monitor network traffic and identify any unusual patterns or malicious activities. They work by analyzing the flow of data across networks, scrutinizing packets for anomalies that may indicate security breaches or cyber attacks. When such anomalies are detected, the NIDS alerts the network administrators, enabling them to investigate and respond swiftly.
The importance of network intrusion detection systems cannot be overstated as they provide organizations with the capability to detect and mitigate potential threats before any significant damage is inflicted. By distinguishing legitimate network activities from suspicious ones, these systems help avert unauthorized access and data leaks. In an era where cyber threats are incessant, network intrusion detection systems offer a proactive approach in fortifying network defenses.
Effective network intrusion detection systems incorporate various technologies, including signature-based and anomaly-based detection methods. Signature-based detection involves identifying known threats by matching network behaviors against a database of known malicious activities. Meanwhile, anomaly-based detection models learn the normal pattern of network behavior and flag deviations. Comprehensive network intrusion detection systems use a combination of these methods to enhance their detection capabilities and maintain the integrity of network resources.
Components of Network Intrusion Detection Systems
1. Detection Engine: The core component of network intrusion detection systems, the detection engine is responsible for analyzing traffic and identifying malicious activities.
2. Alert System: Once an intrusion is detected, network intrusion detection systems utilize an alert system to notify administrators about the potential threat, allowing for immediate action.
3. Database: A database is essential for storing information about known threats. Network intrusion detection systems frequently update their threat databases to stay ahead of new cyber attack vectors.
4. Network Sensors: These are deployed across the network infrastructure to continuously monitor traffic and capture data packets for analysis by the detection engine within network intrusion detection systems.
5. User Interface: A user-friendly interface is crucial for network administrators to interact with network intrusion detection systems effectively, facilitating easy configuration and response actions.
Benefits of Implementing Network Intrusion Detection Systems
Implementing network intrusion detection systems offers numerous advantages. Firstly, they enhance real-time threat detection, allowing organizations to react quickly to potential intrusions. This rapid response capability can significantly reduce the risk of data loss or damage. Additionally, network intrusion detection systems provide comprehensive visibility into network activities, empowering administrators with insights crucial for maintaining network integrity.
Moreover, by continuously analyzing network traffic, network intrusion detection systems support compliance with cybersecurity regulations and standards. Organizations can produce detailed logs and reports as evidence of security measures in place, meeting regulatory requirements more efficiently. Lastly, network intrusion detection systems contribute to building an organization’s reputation by demonstrating a proactive stance in cybersecurity, ensuring stakeholders that their data and communications are adequately protected.
Types of Network Intrusion Detection Systems
Signature-Based NIDS
Signature-based network intrusion detection systems are the traditional choice for many organizations. They rely on a database of known threat patterns to identify malicious activity. While effective against known threats, they require constant updates to the threat database to remain relevant, potentially missing emerging threats.
Anomaly-Based NIDS
Unlike their signature-based counterparts, anomaly-based network intrusion detection systems establish baseline network behavior, flagging deviations as potential threats. They excel in identifying previously unknown threats but can sometimes produce false positives, requiring careful tuning and monitoring to optimize efficacy.
Read Now : Patching Vulnerabilities In Older Software
Hybrid Network Intrusion Detection Systems
Hybrid systems combine the strengths of both signature-based and anomaly-based methodologies. By integrating these approaches, hybrid network intrusion detection systems offer enhanced detection capabilities, improving both the accuracy and speed of threat identification while minimizing false alerts.
Challenges in Network Intrusion Detection Systems
Deploying and managing network intrusion detection systems is not without its challenges. One primary difficulty is handling the volume of data, which can be enormous, especially in large network environments. Processing and analyzing this data in real-time to identify threats requires significant resources and coordination.
Additionally, false positives are a persistent issue in network intrusion detection systems. Anomalies that appear suspicious may not always be malicious, necessitating continuous tuning of detection algorithms to avoid unnecessary disruptions. Keeping up with evolving attack methods also requires frequent updates and enhancements to detection capabilities, which can be resource-intensive.
Furthermore, the integration of network intrusion detection systems with existing network infrastructure can pose difficulties. Compatibility issues and the need for custom configurations may arise, demanding skilled personnel to facilitate smooth operation. Despite these challenges, the benefits of implementing robust network intrusion detection systems far outweigh the hurdles, making them indispensable for cybersecurity.
The Future of Network Intrusion Detection Systems
With advancements in technology, the future of network intrusion detection systems looks promising. The integration of artificial intelligence and machine learning into these systems is currently a focal point, aiming to enhance threat detection accuracy and reduce false positives. AI-enabled network intrusion detection systems are anticipated to learn from each detected threat, becoming increasingly adept at identifying and neutralizing sophisticated cyber attacks.
Moreover, as cloud computing and the Internet of Things (IoT) continue to gain traction, network intrusion detection systems must adapt to secure these evolving environments. Innovations are already underway to extend detection capabilities to virtualized environments, ensuring comprehensive security coverage.
The shift towards a more intelligent, adaptive, and comprehensive approach promises to safeguard networks with unprecedented reliability. As organizations continue to rely heavily on digital infrastructure, network intrusion detection systems will remain a cornerstone of cybersecurity strategies. The investment in developing next-generation systems underscores the commitment to maintaining robust protection against the relentless tide of cyber threats.
Conclusion
In conclusion, network intrusion detection systems are essential components of a robust cybersecurity strategy. They provide the means to detect and respond to potential threats swiftly, safeguarding crucial data and maintaining network reliability. With the ever-growing complexity of cyber threats and the dynamic nature of technology, selecting and maintaining effective network intrusion detection systems is a challenge that organizations must undertake diligently.
A carefully implemented network intrusion detection system not only fortifies networks against threats but also bolsters an organization’s reputation for security, benefiting stakeholders and clients alike. As the landscape of cyber threats evolves, so too must the methods we employ to defend against them, ensuring that network intrusion detection systems remain at the forefront of cybersecurity efforts for years to come.