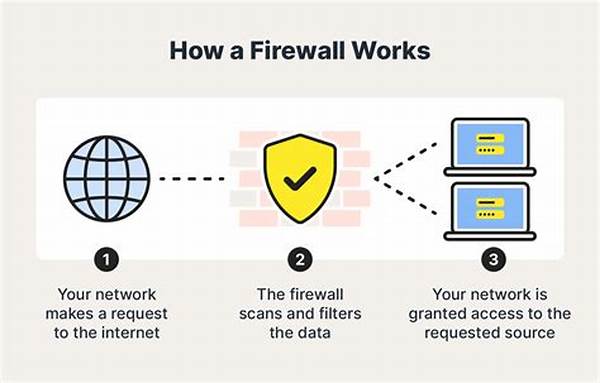
In today’s digital age, securing an organization’s network infrastructure is of utmost importance. Businesses increasingly rely on digital platforms to operate efficiently, making them vulnerable to cyber threats. One of the primary defenses against such threats is an enterprise firewall. Implementing an effective firewall strategy requires careful planning and execution. This document aims to provide comprehensive enterprise firewall implementation guidelines, assisting organizations in safeguarding their networks. By understanding these guidelines, businesses can establish a strong security posture, ensuring the protection of sensitive data and maintaining operational integrity.
Read Now : Customize Rgb Colors For Devices
Importance of Enterprise Firewall Implementation
Enterprise firewall implementation guidelines are crucial for protecting organizational networks from unauthorized access and cyber threats. Firewalls act as the first line of defense, monitoring incoming and outgoing network traffic based on pre-established security rules. These guidelines are essential in defining these rules and ensuring that they align with the specific needs of the organization.
Successfully implementing enterprise firewall guidelines involves selecting the right firewall technology, whether it be hardware or software-based, and configuring it to match organizational requirements. Organizations must also establish processes for regularly updating and maintaining the firewall to protect against emerging threats. Through detailed assessment and planning, companies can customize their firewall settings to protect critical resources while allowing legitimate data flow.
Moreover, enterprise firewall implementation guidelines advocate for regular audits and monitoring. This ongoing vigilance helps in identifying potential vulnerabilities, ensuring that threat management practices adapt to the changing security landscape. By strictly following these guidelines, organizations can mitigate the risk of data breaches, reducing potential financial and reputational damages.
Key Considerations for Implementation
1. Assessment of Network Architecture
Understanding the organizational network architecture is fundamental. Enterprise firewall implementation guidelines stress evaluating routing structures, data flows, and network segmentation to ensure a tailored approach.
2. Selection of Firewall Technology
Choosing the appropriate firewall technology is crucial. Enterprise firewall implementation guidelines help identify whether a traditional, next-generation, or application-based firewall meets the organization’s security and operational needs.
3. Establishment of Security Policies
Crafting robust security policies is vital. The enterprise firewall implementation guidelines assist in developing open, careful access controls, and rule sets aligning with organizational objectives and compliance standards.
4. Regular Monitoring and Updates
Enterprise firewall implementation guidelines highlight the importance of constant monitoring and updating of firewalls. This practice helps in safeguarding against emerging threats and maintaining optimal performance.
5. Training and Awareness
Educating staff about firewall operations and policies is integral. Enterprise firewall implementation guidelines advocate for training programs to ensure that employees operate within the security protocols.
Strategic Planning and Deployment
For any organization, developing a strategic plan is key to successful enterprise firewall implementation. The process starts with a comprehensive risk assessment to evaluate potential vulnerabilities within the network’s architecture and how a firewall can mitigate these risks. Decision-makers should weigh the benefits of different types of firewalls — whether opting for hardware devices or software solutions, understanding what suits the company’s current infrastructure, and potential growth paths.
Enterprise firewall implementation guidelines suggest deploying in phases rather than a one-off attempt. This phased approach offers several advantages, including the ability to adjust and fine-tune configurations without disrupting daily business operations. In each phase, testing is imperative to gauge efficacy. Testing allows organizations to verify that no legitimate traffic is blocked inadvertently and that unauthorized access attempts are uniformly thwarted.
Read Now : Correct Sound Issues With Two Screens
Another focal point of these guidelines is the creation of comprehensive security policies. Policies must outline what constitutes legitimate network traffic and define precise rules on data access permissions. These policies ensure uniformity and compliance across the organization while allowing flexibility for specific roles or departments with unique requirements.
Implementation Challenges and Solutions
Understanding complex network architectures can be challenging. Enterprise firewall implementation guidelines recommend thorough documentation and mapping to facilitate a successful configuration.
As threats evolve, firewalls must adapt. The guidelines underscore the importance of regularly updating firewall technologies and policies to counter new vulnerabilities.
Allocating adequate resources, such as budget and personnel, is necessary. According to the enterprise firewall implementation guidelines, efficient resource allocation ensures uninterrupted firewall management.
Creating policies that strike a balance between security and usability is challenging. Guidelines provide strategies for iterative policy adjustments based on real-world network traffic analysis.
Ensuring staff compliance with security policies is difficult. The enterprise firewall implementation guidelines advocate for ongoing training programs to foster staff understanding and commitment.
Continuous Improvement in Firewall Security
Implementing enterprise firewall guidelines is not a one-time task but an ongoing strategy. Day-to-day operations should include rigorous firewall monitoring and logging. Such vigilance is essential not only to identify and respond to security incidents swiftly but also to understand traffic patterns and adjust configurations proactively. Many organizations benefit from integrating firewall logs with broader security information and event management (SIEM) systems for a holistic security approach.
Beyond the technical aspects, the human element plays a crucial role in firewall security. Enterprise firewall implementation guidelines emphasize building a culture of security within the organization. Teams should be encouraged to stay informed about the latest threats and encouraged to contribute to security policies. This proactive stance is instrumental in creating a resilient security framework that adapts along with evolving threats.
In conclusion, the execution of enterprise firewall implementation guidelines is an extensive and ongoing endeavor. This multifaceted approach ensures security measures evolve hand in hand with technological advancements and emerging threats. By fostering a culture of security awareness and engagement, organizations can safeguard their digital assets effectively.
Benefits of Adhering to Guidelines
Achieving effective enterprise firewall implementation can yield numerous benefits for an organization. Adhering to established guidelines can make a significant difference in overall security posture. Firstly, these guidelines offer a structured approach to configuring and managing firewall systems, which in turn helps prevent unauthorized access and mitigate the risks associated with cyber threats. Furthermore, organizations benefit from enhanced compliance with industry regulations and standards, as the guidelines typically align with security best practices.
Another critical benefit is the optimization of network performance. By effectively segmenting network traffic and applying the right rules, organizations can ensure seamless data flow, which reduces latency and enhances user experience. Properly managed firewall configurations also contribute to reducing the likelihood of costly and disruptive security incidents. Finally, these guidelines foster a proactive security culture among employees, which is vital for organizational resilience in the face of potential threats.
Summary
In summary, enterprise firewall implementation guidelines serve as a cornerstone of organizational network security. They provide a blueprint for building robust defenses against cyber threats. By following these guidelines, organizations can achieve a balance between strong security and operational efficiency. The guidelines emphasize critical factors such as technology selection, policy development, and continuous monitoring. Each aspect plays a vital role in creating a secure environment that protects sensitive information and ensures business continuity.
Furthermore, the successful implementation of enterprise firewall guidelines requires commitment from every level of the organization. From top management to individual employees, everyone must understand their role in maintaining security. By fostering a security-conscious culture, organizations can leverage these guidelines to stay ahead of potential threats. Ultimately, adhering to enterprise firewall implementation guidelines protects not only the organization’s data but its reputation and future growth.