Embracing Modern Cybersecurity Strategies
In the ever-evolving realm of digital security, innovative approaches to cybersecurity architecture optimization stand as pivotal in safeguarding sensitive data and systems. These strategies hold the potential to transform conventional methods by integrating advanced technologies and tailoring solutions to cater to the specific needs of organizations. At the heart of this evolution lies the ability to preemptively identify vulnerabilities and design multilayered security measures that adapt to the complexities of modern digital landscapes.
Read Now : Instantaneous Protection Options Setup
The essence of innovative approaches to cybersecurity architecture optimization is the seamless fusion of technology and strategy. This includes employing artificial intelligence for real-time threat detection, leveraging machine learning to anticipate potential breaches, and adopting zero-trust models that assume no entity is trustworthy by default. Each approach, coupled with robust encryption practices, ensures that information integrity is maintained, allowing organizations to operate with heightened confidence in their cybersecurity defenses.
Moreover, these innovative approaches to cybersecurity architecture optimization emphasize continuous monitoring and rapid response to emergent threats, thereby minimizing damage. By constantly evolving and testing their security architectures, organizations can stay steps ahead of cybercriminals, turning potential attackers’ obstacles into opportunities for reinforcement. Such forward-thinking strategies not only protect assets but also enhance reputations, providing customers and partners with peace of mind in an era where data breaches are prevalent.
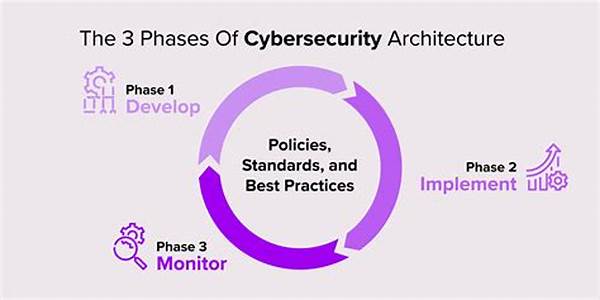
Key Components of Cybersecurity Optimization
1. Integration of AI and Machine Learning: These technologies form the backbone of innovative approaches to cybersecurity architecture optimization by offering predictive analytics that foresees and mitigates threats before they materialize.
2. Adoption of Zero-Trust Architecture: Building a model where trust is never implicit offers unparalleled security, embodying the essence of innovative approaches to cybersecurity architecture optimization.
3. Robust Encryption Techniques: Implementing advanced encryption is crucial in innovative approaches to cybersecurity architecture optimization, ensuring data remains secure during transmission and storage.
4. Continuous Monitoring and Prompt Response: These strategies are vital, as part of innovative approaches to cybersecurity architecture optimization, to safeguard against new threats and vulnerabilities that develop over time.
5. Tailored Cybersecurity Solutions: Customized strategies reflect the organization’s specific needs, demonstrating innovative approaches to cybersecurity architecture optimization by aligning with unique operational dynamics.
Overcoming Challenges in Cybersecurity
Despite the promise held by innovative approaches to cybersecurity architecture optimization, organizations often face challenges in integration. The complexities of legacy systems represent a notable hurdle. As businesses strive to adopt new methodologies, they may find their existing infrastructure resistant, requiring comprehensive assessments before transitioning smoothly. However, strategic planning and phased implementations can effectively mitigate these challenges.
Furthermore, the human element remains crucial. Employees must be educated and trained in the latest security protocols to complement innovative approaches to cybersecurity architecture optimization. Continuous education ensures that staff remain vigilant and are equipped to respond appropriately to any threats, thereby enhancing the overall resilience of the cybersecurity framework.
A clear understanding of regulatory landscapes and compliance requirements is essential when implementing innovative approaches to cybersecurity architecture optimization. Adherence to international standards ensures that companies maintain a robust security posture while meeting legal obligations, further underscoring the importance of a holistic approach that encompasses technology, education, and regulation in cybersecurity.
Practical Applications of Cybersecurity Optimization
Implementing innovative approaches to cybersecurity architecture optimization involves several essential practices. Organizations should start with the integration of AI-driven solutions, which provides them with predictive capabilities and threat analysis precision. AI empowers cybersecurity systems to evolve continuously, recognizing patterns and outlier behaviors that humans might miss.
Data encryption is a non-negotiable element in innovative approaches to cybersecurity architecture optimization. Effective encryption safeguards data at rest and in transit, ensuring unauthorized entities cannot access or decipher sensitive information. Coupled with robust access controls, encryption fortifies an organization’s defense mechanisms.
The incorporation of a zero-trust framework is a cornerstone of innovative approaches to cybersecurity architecture optimization. By verifying each user and device attempting access to the system, organizations minimize the chance of unauthorized intrusion. This model aligns with the principle of least privilege, which limits access to sensitive resources based on necessity.
Read Now : “factors In Comparing Computer Specs”
Data segmentation plays a critical role, complementing innovative approaches to cybersecurity architecture optimization by preventing the lateral movement of potential threats within the system. This compartmentalization ensures that even if a breach occurs, its impact is minimized.
Regular audits and vulnerability assessments are integral to maintaining a strong security posture. These activities enable organizations to identify existing weaknesses and rectify them promptly, reflecting a commitment to the principles of innovative approaches to cybersecurity architecture optimization.
Future Trends in Cybersecurity Optimization
As the digital landscape continues to transform, so must the strategies surrounding innovative approaches to cybersecurity architecture optimization. One emerging trend is the rise of quantum computing, which presents both challenges and opportunities for cybersecurity. While quantum technology promises superior computational power, it also threatens current encryption standards, necessitating advancements in cryptographic protocols.
Blockchain technology is another frontier in innovative approaches to cybersecurity architecture optimization. Its inherent features—decentralization, transparency, and immutability—can offer robust solutions for secure transactions and data storage. By employing blockchain, organizations can enhance data integrity and trust within their networks.
The Internet of Things (IoT) amplifies the need for innovative approaches to cybersecurity architecture optimization as interconnected devices increase the attack surface. Implementing secure and standardized communication protocols across IoT devices can avert potential security breaches and ensure sustained privacy.
Additionally, the shift towards remote work since the onset of the global pandemic has underscored the importance of innovative approaches to cybersecurity architecture optimization. Securing remote access points, utilizing VPNs, and ensuring endpoint security remain at the forefront of developing comprehensive security architectures.
Ultimately, proactive engagement in continuous learning and adaptation stands as crucial for organizations to navigate the future landscape effectively. By embracing innovative approaches to cybersecurity architecture optimization, businesses can prepare for uncertainties and fortify themselves against the ever-present cyber threats.
Conclusion
In conclusion, the domain of innovative approaches to cybersecurity architecture optimization is not only dynamic but crucial for the protection of digital infrastructures. By integrating cutting-edge technologies such as AI, zero-trust models, and robust encryption practices, organizations can develop flexible and effective security measures. These approaches must also consider regulatory compliance and staff training, ensuring a comprehensive and adaptable security framework.
Organizations must remain vigilant, actively monitoring and updating their cybersecurity strategies to optimize their architectural defenses. The future of cybersecurity will demand even more creativity and innovation as threats become increasingly sophisticated. Emphasizing a unified strategy that balances technology, human factors, and regulatory obligations can immeasurably enhance organizations’ ability to mitigate risks.
Summary
In the contemporary digital environment, innovative approaches to cybersecurity architecture optimization have become essential. By adopting AI-driven solutions, zero-trust frameworks, and advanced encryption, organizations can safeguard their assets and maintain data integrity. It’s essential to continually assess and update security strategies to enhance defense mechanisms against sophisticated cyber threats.
The intersection of technology and strategic implementation forms the backbone of innovative approaches to cybersecurity architecture optimization. As threats evolve, maintaining a dynamic and adaptive security posture will ensure organizational resilience. Furthermore, these strategies require organizational commitment to training and compliance, guaranteeing robust defense against myriad online dangers.