In today’s digital world, the threat of malware looms large over individuals and organizations alike. Understanding and combating these threats necessitates a detailed examination of the malware itself. The in-depth malware analysis process stands as a pivotal practice in defending against these malicious actors. By dissecting malware, we can unravel its methods of operation, understand its impact, and develop strategies to mitigate and eliminate its effects. In this article, we will explore the various facets of the in-depth malware analysis process, providing insights into its critical role in cybersecurity.
Read Now : Uninstall Unused Windows Applications
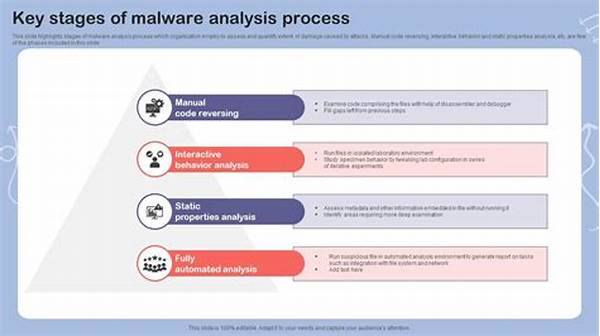
Key Stages of the In-Depth Malware Analysis Process
The in-depth malware analysis process comprises several critical stages, each contributing uniquely to understanding and mitigating the threat posed by malware. The first stage involves collecting samples, which is crucial for obtaining the malicious software that requires analysis. This is followed by a behavioral analysis, where the aim is to observe how the malware operates in a controlled environment. This step is vital in recognizing potential damage and pathways the malware might exploit.
Next comes the static analysis phase, where analysts delve into the malware’s binary code without executing it. This process often involves examining the code structure, embedded resources, and identifying potentially harmful patterns. Dynamic analysis follows, which involves executing the malware in a secure setting to observe its real-time behavior. This step can reveal additional insights that static analysis alone might miss, such as concealed operations and network communications.
Finally, the reporting and documentation stage is integral to the in-depth malware analysis process. Here, analysts compile their findings into a comprehensive report, detailing the nature and potential impact of the malware. Such documentation not only aids in addressing the current threat but also serves as a reference for future analyses.
Techniques Employed in the In-Depth Malware Analysis Process
1. Static Analysis: Examines the malware’s code and structure without executing it, providing insights into its construction.
2. Dynamic Analysis: Involves running the malware in a controlled environment to observe its real-time behavior and effects.
3. Behavioral Analysis: Focuses on understanding how malware interacts with systems, revealing potential vulnerabilities.
4. Reverse Engineering: A meticulous approach used to deconstruct malware to understand its components and functionality.
5. Network Analysis: Studies the communication patterns of malware to highlight how it spreads or gathers data.
Challenges in the In-Depth Malware Analysis Process
Undertaking the in-depth malware analysis process is not without its challenges. One of the most significant obstacles is the ever-evolving nature of malware. Malicious developers continuously adapt and innovate, creating sophisticated malware variants designed to evade detection. This requires analysts to stay ahead of these developments, often involving advanced training and adopting cutting-edge tools.
Moreover, the sheer volume of malware threats presents a logistical challenge. With hundreds of thousands of new threats identified annually, analysts are often overwhelmed. This abundance necessitates prioritization and automation to maximize efficiency without compromising thoroughness. Automation tools can perform preliminary analyses, allowing human analysts to focus on more complex and nuanced threats.
Read Now : Utilizing Task Manager Effectively
Additionally, ensuring a safe and controlled environment for analysis is another crucial aspect that requires attention. The in-depth malware analysis process must ensure that no harm comes to the systems used for analysis and that malware doesn’t unintentionally spread. This calls for careful planning and robust security protocols, which can be resource-intensive and costly.
Tools Utilized in the In-Depth Malware Analysis Process
The in-depth malware analysis process heavily relies on various tools to enhance accuracy and efficiency. Tools such as debuggers and disassemblers are employed during static and dynamic analyses, providing insights into the malware’s behavior and structure. Sandboxes, which simulate real-world environments, are crucial for safely examining malware’s operational patterns.
Benefits of the In-Depth Malware Analysis Process
Engaging in an in-depth malware analysis process offers numerous advantages, primarily in fortifying an organization’s defenses against cyber threats. Through meticulous analysis, organizations can develop targeted security measures, leading to more resilient network defenses. By understanding the intricacies of malware, organizations can devise strategies that not only address current threats but also preemptively guard against future attacks.
Moreover, the process fosters an informed and proactive security strategy. Knowledge gained through analysis can inform training programs, helping staff recognize warning signs of malware infections. This depth of understanding elevates the overall cybersecurity posture, ensuring preparedness for evolving threats.
Conducting a Thorough In-Depth Malware Analysis Process
A thorough in-depth malware analysis process is foundational in the fight against cyber threats. Analysts must employ a combination of techniques, such as static and dynamic analyses, to capture a comprehensive picture of the malware. Critical to this process is the collaboration among cybersecurity professionals, as sharing insights can lead to more robust defenses.
Moreover, continuous education and training are vital in keeping pace with malicious actors. The landscape of cyber threats is fluid, and staying informed is imperative. By cultivating a culture of learning, organizations equip themselves with the tools and knowledge necessary to combat known and emerging threats effectively.
Conclusion: The Imperative of the In-Depth Malware Analysis Process
In summation, the in-depth malware analysis process stands as a cornerstone in the defense against cyber threats. By delving into the intricacies of malware, this process empowers organizations to understand and circumvent potential harms. It enables the development of robust security protocols tailored to counteract threats and safeguard sensitive information.
The process not only addresses immediate concerns but fosters a culture of vigilance and preparedness. As cyber threats continue to evolve, the adaptability and foresight provided by the in-depth malware analysis process remain indispensable. Continuous investment in this process ensures a resilient cybersecurity infrastructure, capable of withstanding the challenges of an ever-changing cyber landscape.