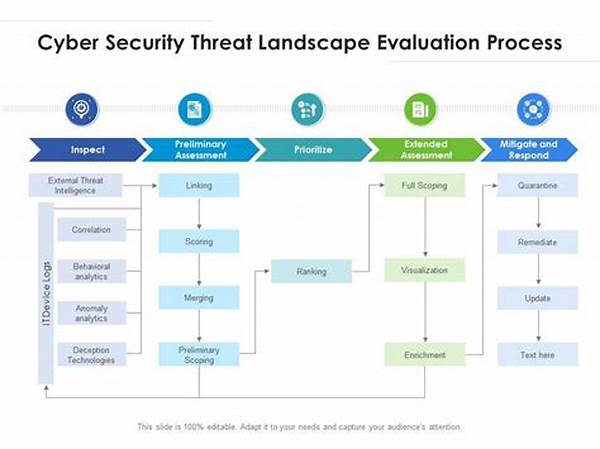
In the rapidly evolving digital landscape, addressing cybersecurity concerns has become paramount for organizations worldwide. Scheduled cyber threat evaluations are an essential component of a robust cybersecurity strategy. They provide businesses with a structured approach to identifying, assessing, and mitigating potential threats. By scheduling regular assessments, companies ensure they stay one step ahead of cybercriminals. This approach not only enhances security measures but also builds trust with customers, who are increasingly concerned about data privacy and security.
Read Now : Gaming Setup For Spinal Health
Importance of Regular Evaluations
Conducting scheduled cyber threat evaluations is crucial for maintaining a secure IT environment. These assessments help organizations identify vulnerabilities in their systems and applications. By analyzing potential threats and weaknesses, companies can implement the necessary measures to mitigate risks. Scheduled evaluations also facilitate compliance with industry regulations and standards, ensuring businesses are not just reacting to incidents but proactively preventing them. Regular evaluations are a testament to a company’s commitment to its stakeholders, demonstrating a proactive stance in safeguarding digital assets.
Firstly, scheduled cyber threat evaluations help in early detection of potential threats. Identifying risks early allows organizations to address vulnerabilities before they become critical issues.
Secondly, these evaluations ensure compliance with regulatory requirements. Regular assessments align business practices with industry standards, avoiding penalties.
Thirdly, scheduled cyber threat evaluations enhance the trust between the organization and its clients. Customers feel secure knowing that their data is protected by regular checks.
Fourthly, they streamline the process of updating security protocols. Consistent evaluations highlight areas for improvement, making security updates more efficient.
Lastly, these evaluations encourage a culture of security awareness. Regular reviews keep cybersecurity on the agenda, emphasizing its importance across the organization.
Methodology of Evaluations
The methodology behind scheduled cyber threat evaluations involves a systematic approach. Initially, organizations conduct a thorough analysis of existing infrastructure to identify potential entry points for attackers. This is followed by ethical hacking or penetration testing to simulate real-world attacks. By doing so, businesses can measure their resilience to cyber threats. Next, comprehensive reports are generated, detailing findings and offering recommendations for improvement. These recommendations form the basis for strategic decision-making, ensuring that vulnerabilities are addressed proactively rather than reactively.
Moreover, collaboration with third-party cybersecurity experts often augments internal evaluations. These experts bring a fresh perspective and specialized skills, offering insights that might be overlooked internally. Their involvement ensures that the evaluation process adheres to current best practices and leverages the latest technological advancements in cybersecurity. Scheduled evaluations therefore serve as a crucial framework for continuous improvement, facilitating both operational security enhancements and strategic planning.
Evaluation Techniques
1. Vulnerability Scanning: Scheduled cyber threat evaluations begin with scanning networks and systems for known vulnerabilities, a foundational step in identifying potential risks.
2. Penetration Testing: Employed to mimic attacks, penetration testing during scheduled cyber threat evaluations reveals how systems might withstand real cyber threats.
3. Risk Assessment: This step evaluates the potential impact of vulnerabilities identified in the scheduled cyber threat evaluation process, guiding prioritization.
4. Reporting and Analysis: Detailed reports are compiled post-evaluation, providing actionable insights on identified weaknesses and mitigation strategies.
5. Remediation Planning: Following analysis, a strategic plan is crafted to address and remediate vulnerabilities identified during the scheduled cyber threat evaluation.
Read Now : Troubleshoot Slow Windows Startup
6. Security Policy Review: Evaluations often include a review of existing security policies, ensuring alignment with industry best practices.
7. Compliance Check: Scheduled evaluations incorporate checks against regulatory requirements, confirming adherence to necessary cybersecurity standards.
8. Employee Training: Part of the evaluation might involve assessing and improving employee awareness and training programs regarding cybersecurity.
9. Incident Response Testing: Testing response mechanisms is crucial; simulated incidents during evaluations test an organization’s readiness.
10. Feedback Loop Creation: Establishing a feedback loop from scheduled cyber threat evaluations supports continuous improvement in security posture.
Continuous Improvement and Future Planning
Scheduled cyber threat evaluations are not a one-time event; they embody a continuous cycle of improvement. Each evaluation forms the foundation for future assessments, providing historical data that informs trends and patterns in cyber threats. By leveraging this information, organizations can predict potential future vulnerabilities and implement preemptive strategies. This forward-thinking approach ensures that not only are current threats mitigated, but emerging threats are anticipated.
The insights gained from these scheduled evaluations contribute significantly to strategic planning. They guide resource allocation, ensuring that security measures are prioritized according to risk. Organizations can make informed decisions about investing in new technologies or enhancing existing infrastructures. Additionally, scheduled evaluations encourage a culture of security awareness within the organization. As employees become more familiar with potential threats, they adopt best practices in their daily operations, fundamentally strengthening the organization’s security posture.
The Role of Technology
Technology plays a pivotal role in scheduled cyber threat evaluations. Advanced tools and software automate the detection and analysis of vulnerabilities, enhancing the efficiency and accuracy of evaluations. Machine learning algorithms, for instance, can predict potential attack vectors based on historical data. These technologies not only make evaluations more effective but also allow them to be conducted more frequently. As a result, organizations can maintain a dynamic understanding of their threat landscape, adjusting their strategies as needed.
Furthermore, technological advancements facilitate real-time monitoring and threat intelligence sharing. During a scheduled cyber threat evaluation, access to timely information about emerging threats enables organizations to stay ahead of cybercriminals. Integration with global threat intelligence networks enhances the ability to respond swiftly and effectively. Scheduled evaluations, therefore, are crucial in a world where cyber threats are continuously evolving, highlighting the necessity of cutting-edge technology in maintaining a robust cybersecurity posture.
Summary and Recommendations
Scheduled cyber threat evaluations are integral to securing an organization’s digital assets. They offer a systematic approach to identifying and mitigating risks, ensuring businesses are prepared against potential cyber threats. By conducting regular assessments, organizations demonstrate a proactive commitment to cybersecurity, building trust with stakeholders.
In essence, scheduled cyber threat evaluations serve as a defensive and strategic tool. They not only protect current operations but also inform future security measures, allowing organizations to anticipate and adapt to a continually changing threat landscape. By prioritizing these evaluations, companies ensure a robust defense against the ever-present risk of cyber attacks, safeguarding not only their assets but also their reputation and customer trust.