In today’s digital age, protecting sensitive information from threats has become a top priority for organizations. The rise in cybercrime has emphasized the need for a rigorous defence mechanism. One solution that stands out is the implementation of comprehensive security scanning protocols. These protocols help identify vulnerabilities in a system, allowing organizations to address them before they can be exploited by malicious actors. This article delves into the essential components and benefits of adopting such protocols to safeguard digital assets effectively.
Read Now : Reduce Strain In Gaming Sessions
Understanding Comprehensive Security Scanning Protocols
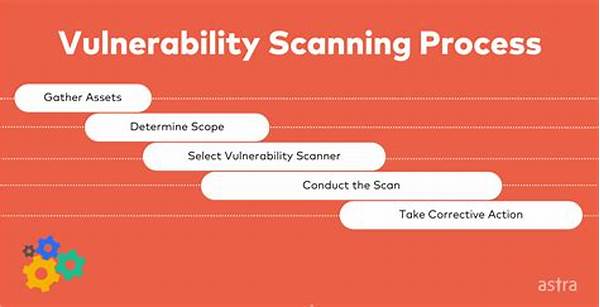
Comprehensive security scanning protocols are structured methodologies designed to conduct extensive evaluations of systems and networks. These protocols utilize a variety of tools and techniques to scan for potential vulnerabilities, misconfigurations, and unusual activities that may pose threats. By systematically identifying weaknesses, organizations can take proactive measures to enhance their security posture. Furthermore, these protocols help ensure compliance with industry standards and regulations, which is critical in today’s business environment. Implementing comprehensive security scanning protocols not only mitigates risks but also instills confidence among clients and stakeholders that their data is being protected with the highest standards.
Key Elements of Comprehensive Security Scanning Protocols
1. Regular Updates: Stay ahead of vulnerabilities by ensuring that comprehensive security scanning protocols are updated frequently to detect new threats.
2. Automated Tools: Leverage high-quality automated tools designed to perform thorough scans as part of comprehensive security scanning protocols, ensuring time-efficient and accurate results.
3. Penetration Testing: Conduct regular penetration testing to simulate attacks and assess the effectiveness of comprehensive security scanning protocols in real-world scenarios.
4. User Training: Educate employees on the importance of security best practices and their role within comprehensive security scanning protocols to prevent user-related vulnerabilities.
5. Risk Assessment Reports: Develop detailed reports that highlight identified risks, providing a clear overview of what comprehensive security scanning protocols have uncovered for strategic planning.
Importance of Regular Audits in Security Scanning
Regular audits play a vital role in the effectiveness of comprehensive security scanning protocols. These audits allow for the frequent assessment of networks and systems, ensuring that any new vulnerabilities are quickly identified and addressed. Conducting routine audits aids in maintaining compliance with security standards, which is crucial in avoiding potential fines and damages to reputation. Moreover, they assist in validating the integrity of the system by ensuring all components of the security system are functioning as expected. Integrating regular audits into comprehensive security scanning protocols results in more resilient, adaptable security strategies capable of addressing evolving threats efficiently.
Moreover, audits provide an opportunity to refine existing protocols. By analyzing audit results, organizations can pinpoint specific areas for improvement, which contributes to the continual enhancement of their security framework. Through a proactive approach, comprehensive security scanning protocols become a vital part of the organization’s overall cybersecurity strategy.
Challenges and Solutions within Comprehensive Security Scanning Protocols
Although comprehensive security scanning protocols are pivotal, they come with their own set of challenges.
1. Complexity: Implementing comprehensive security scanning protocols can be complex. Consistently updating and maintaining them requires significant resources and expertise.
2. Cost: Deploying thorough scanning protocols can involve substantial investment in technology and personnel.
3. False Positives: Scans can sometimes report vulnerabilities that are not threats, which may lead to unnecessary resource allocation.
4. User Resistance: There can be resistance from employees in adhering to new security measures, potentially impacting the effectiveness of comprehensive security scanning protocols.
Read Now : Resolve Windows Performance Problems
5. Integration Issues: Difficulty in integrating new protocols with existing systems may arise, necessitating additional time and effort.
6. Data Privacy Concerns: Ensuring that comprehensive security scanning protocols do not infringe on user privacy is essential, requiring a balanced approach.
7. Continuous Monitoring Needs: Comprehensive security scanning protocols require continuous monitoring, which demands constant vigilance and real-time insights into system activities.
8. Changing Threat Landscape: The ever-evolving nature of cyber threats means that comprehensive security scanning protocols must be adaptive and flexible.
9. Human Error: Even with the best protocols, human error remains a persistent risk, underlining the importance of robust user education.
10. Regulatory Compliance: Ensuring protocols are in line with changing regulations can be challenging, necessitating constant adjustments.
Benefits and Future Direction of Comprehensive Security Scanning Protocols
The implementation of comprehensive security scanning protocols offers numerous benefits. It not only reduces the risk of data breaches but also helps maintain customer trust and loyalty. Additionally, these protocols provide valuable insights into the organization’s security environment, facilitating informed decision-making. Looking to the future, leveraging artificial intelligence and machine learning can enhance the efficacy of these protocols by automating complex tasks and identifying patterns that would be missed during manual scans. Innovations in these areas hold great promise for the evolution of comprehensive security scanning protocols, allowing them to tackle even more sophisticated threats with greater agility.
Furthermore, organizations must focus on building a security-conscious culture. By fostering an environment where security is everyone’s responsibility, the protocols can be more effectively implemented and any potential security risks can be minimized. The fusion of technology, strategy, and culture ensures a robust defense against cyber threats now and in the future.
Comprehensive Security Scanning Protocols in the Modern Landscape
As we navigate an increasingly digital world, the reliance on comprehensive security scanning protocols is more pronounced than ever. Their role in safeguarding data integrity and combating cyber threats is indispensable for organizations across all sectors. Traditional approaches to security are no longer sufficient; instead, a dynamic and adaptable set of protocols must be embraced. This involves staying informed about the latest trends in cybersecurity and embedding security measures seamlessly into day-to-day operations. Emphasizing a holistic approach ensures that every layer of the organization’s infrastructure is protected.
Moreover, the collaborative effort between IT departments, executive management, and external security experts can enhance the effectiveness of comprehensive security scanning protocols. By pooling resources and expertise, organizations can craft resilient security strategies that are both proactive and reactive. Building robust partnerships with trusted security vendors can also provide access to cutting-edge solutions, ensuring that organizations remain one step ahead in the cybersecurity race.
Conclusion: Securing the Future with Comprehensive Security Scanning Protocols
In conclusion, the adoption of comprehensive security scanning protocols is crucial for mitigating the risks associated with cyber threats. Their continuous evolution and integration into organizational operations will be vital in countering sophisticated attacks. A strong emphasis on regular audits, user education, and strategic investments in technology will help ensure these protocols are both effective and sustainable in the long term. Above all, creating a culture where security is deeply ingrained and prioritized will pave the way for a secure digital future.