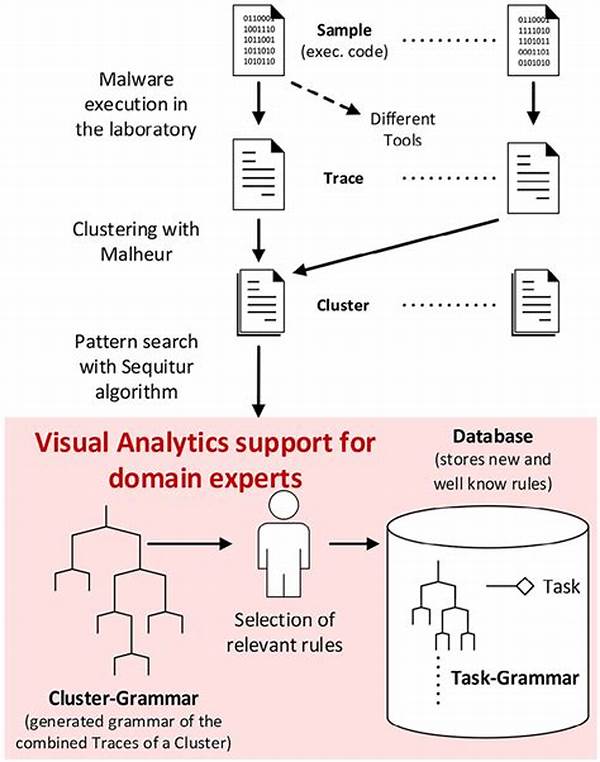
Understanding how malware operates is crucial in the field of cybersecurity. One approach to dissecting malware is through behavioral patterns of malware analysis. This method involves observing the actions and characteristics of malware in a controlled environment to comprehend its impact. By analyzing these patterns, specialists can predict potential threats and develop effective countermeasures. In the following sections, we will delve into various aspects of malware’s behavioral patterns to provide a comprehensive overview of this critical cybersecurity method.
Read Now : Boost Windows App Processing Speed
Exploring Behavioral Patterns of Malware
At the heart of cybersecurity, understanding malware’s behavior is crucial. Analyzing the behavioral patterns of malware often involves studying how malicious software interacts with its environment. This type of analysis provides deep insights into the malware’s operational mechanism, which aids in detecting and mitigating potential threats. Behavioral patterns of malware analysis involve observing how malware executes, including changes it makes to file systems, registry keys, and network activity. By focusing on these indicators, cybersecurity professionals can identify and isolate malicious activities before they cause significant damage.
Malware often disguises itself to bypass traditional security measures. This makes the behavioral patterns of malware analysis a valuable tool. By creating an environment that mimics typical user behavior, cybersecurity experts can lure malware into revealing its true functionality. This process enables the identification of variants and helps in crafting targeted defenses. Furthermore, by cataloging how different malware types behave, researchers can predict new forms of attacks, ensuring that defenses remain robust against evolving threats.
Behavioral patterns of malware analysis do not only stop at detection but also aid in the development of recovery strategies. By understanding the full cycle of malware activity, from entry to execution and spread, professionals can establish effective remediation processes. This is vital for minimizing downtime and preserving data integrity, ultimately contributing to a resilient cybersecurity strategy. The ongoing study and documentation of these patterns help in creating a comprehensive knowledge base that benefits the cybersecurity community worldwide.
Key Aspects of Behavioral Patterns of Malware
1. Execution Behavior: Understanding how malware executes is crucial. It involves examining how malicious software carries out tasks and manipulates system resources.
2. Persistence Mechanisms: Experts focus on identifying how malware ensures it remains active within an infected system over time using various methods.
3. Network Activity: Analyzing communication attempts of malware with external servers or systems is essential to determine its objectives.
4. Evasion Techniques: Identifying strategies used by malware to avoid detection is a critical aspect of behavioral patterns of malware analysis.
5. Impact on System Integrity: Assessing how malware alters or compromises system files and operations indicates the severity and intent of an attack.
The Importance of Behavior-Based Detection
In the continuously evolving landscape of cybersecurity threats, traditional signature-based detection methods struggle to keep up with new and sophisticated malware. This is where behavioral patterns of malware analysis play an indispensable role. By focusing on the behaviors rather than the specific code signature, this approach provides a more dynamic and adaptable line of defense.
Behavioral analysis unveils the real-time intentions of malware, offering a preventive approach to cybersecurity. It is crucial in identifying zero-day vulnerabilities, which are often exploited before solutions are available in signature databases. This method allows security teams to be proactive rather than reactive, mitigating risks before they escalate into severe security breaches. By understanding how malware behaves, cybersecurity measures can be fine-tuned, making defenses more resilient and less prone to failure.
The insights gained from analyzing behavioral patterns are not only beneficial for immediate threat mitigation but are also invaluable for long-term strategic planning. This involves refining security protocols and preparing for future unknown threats. As attacks become more advanced, the reliance on behavioral patterns of malware analysis becomes more pronounced. It is a field that necessitates continuous research and adaptation to stay ahead of an ever-changing threat landscape.
Implementing Behavioral Analysis Techniques
Utilizing behavioral patterns of malware analysis involves implementing a variety of techniques to identify and neutralize threats efficiently. Here are ten key approaches:
1. Sandboxing: An isolated environment used to execute and analyze malware without risking the host system.
2. Dynamic Analysis: Observing malware behavior during runtime to gather intelligence.
3. Event Logging: Monitoring system logs to detect irregular activities triggered by malware.
4. Heuristic Analysis: Implementing algorithms to detect malware based on behavior rather than known signatures.
Read Now : Access Control Systems And Policies
5. Real-Time Monitoring: Continuously watching system activities and network traffic for suspicious patterns.
6. Backtracking: Identifying the entry point of malware for a full understanding of its infection path.
7. System Impact Assessment: Evaluating the changes made to the system to assess malware severity.
8. Network Forensics: Analyzing data packets to understand malware communication.
9. Threat Intelligence Sharing: Collaborating with other security entities to enhance malware understanding.
10. Behavioral Profiling: Creating profiles based on malware behavior to predict future threats.
Strategies for Advancing Malware Analysis
The importance of advancing behavioral patterns of malware analysis cannot be overstated in the current age of cybersecurity challenges. As malware continues to evolve, so must the methods used to analyze and counteract it. Engaging in proactive strategies is essential for staying ahead of cybercriminals who constantly develop more sophisticated attacks to penetrate security barriers.
One effective strategy is investing in cutting-edge research and technology that focuses on the behavioral nuances of malware. Enhanced machine learning algorithms can be employed to create more accurate behavioral profiles, which improve detection rates and reduce false positives. Furthermore, integrating artificial intelligence into the analysis process allows for the rapid processing of vast data sets, helping security professionals to identify complex patterns that may go unnoticed.
Moreover, fostering a collaborative environment within the cybersecurity community is crucial. Sharing insights and research findings related to behavioral patterns of malware analysis can lead to the development of more robust defenses across the board. By pooling resources and knowledge, cybersecurity practitioners can collectively work towards more effective threat detection and mitigation strategies, creating a unified front against emerging malware challenges.
Conclusion on Behavioral Patterns of Malware Analysis
The concept of behavioral patterns of malware analysis encompasses a sophisticated approach to identifying and mitigating cybersecurity threats. By focusing on how malware acts rather than relying solely on known signatures, this method enhances the ability to detect and respond to threats that might otherwise go unnoticed. In the rapidly changing landscape of cyber threats, adapting advanced techniques like behavioral analysis is more critical than ever.
As cybersecurity threats become increasingly complex, the need for a proactive, behavior-based approach becomes paramount. Enhanced detection mechanisms allow for better anticipation of zero-day attacks, providing organizations with an edge. Ultimately, the collective effort towards advancing behavioral patterns of malware analysis, supplemented by continuous research, collaboration, and technological innovation, can significantly fortify defenses and safeguard against the evolving landscape of cyber threats.
Summary of Behavioral Patterns in Malware Analysis
In conclusion, the analysis of behavioral patterns in malware provides essential insights into the operational methodologies of cyber threats. By focusing on the behaviors and actions taken by malware, rather than mere signatures, analysts can devise more flexible and durable security measures. This adaptability is crucial in an era where malware continuously morphs to evade detection.
Moreover, the use of behavioral patterns of malware analysis fosters advancements in predictive security measures. Organizations can better prepare for unknown threats, minimizing the risk of severe disruptions caused by cyber-attacks. This approach builds resilience and reduces the likelihood of successful infiltrations by malicious entities.
The continuous study and application of behavioral patterns in malware analysis reinforce the broader cybersecurity infrastructure. It encourages collaboration among professionals and promotes the development of more refined and efficient security solutions. As we move forward with an ever-increasing dependency on digital landscapes, embracing these analytical techniques is indispensable for maintaining robust defenses against the sophisticated and persistent threats of malware.