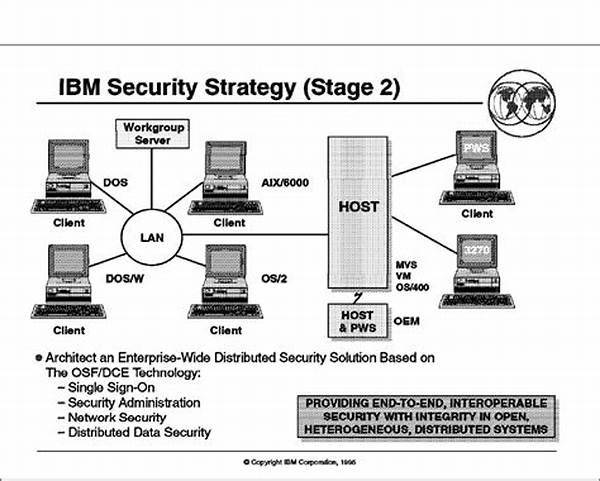
In an increasingly interconnected digital world, safeguarding sensitive information is paramount. Enterprises today face multifaceted threats that require robust security measures. As organizations strive to protect their data and maintain stakeholder trust, the adoption of comprehensive security standards across the organization becomes crucial. Enterprise-wide security protocol standards play a vital role in ensuring the protection and integrity of data within large-scale organizations.
Read Now : Comparing Gaming Peripherals Response Time
Importance of Enterprise-Wide Security Protocol Standards
Enterprise-wide security protocol standards are indispensable for maintaining a cohesive and resilient security posture. By establishing uniform security protocols, organizations can mitigate risks associated with data breaches and cyber threats. These standards facilitate consistent security practices across all divisions and departments, ensuring that sensitive information is equally protected irrespective of where it resides within the enterprise.
Implementing enterprise-wide security protocol standards also enhances operational efficiency. When every employee understands and follows the same security protocols, it reduces the likelihood of human errors that could lead to security breaches. Moreover, these standards simplify compliance with regulatory requirements, as organizations can demonstrate adherence to industry best practices, which is often crucial during audits and inspections.
Furthermore, adopting these standards strengthens an organization’s reputation and builds customer trust. In today’s digital landscape, consumers are increasingly concerned about the privacy and protection of their data. By publicly demonstrating a commitment to comprehensive security measures, organizations can differentiate themselves from competitors and foster long-term loyalty among their clients.
Key Components of Enterprise-Wide Security Protocol Standards
1. Risk Assessment: Conducting thorough assessments to understand vulnerabilities across the enterprise is essential for formulating effective security strategies.
2. Access Control: Implementing strict access controls ensures only authorized personnel can access sensitive data and systems.
3. Data Encryption: Encrypting data both at rest and in transit safeguards information from unauthorized access.
4. Incident Response Plan: A well-defined plan enables prompt and effective responses to security incidents, minimizing potential damage.
5. Continuous Monitoring: Ongoing surveillance and analysis help in quickly identifying and addressing emerging threats and vulnerabilities.
Developing Effective Enterprise-Wide Security Protocol Standards
Creating enterprise-wide security protocol standards is a comprehensive process involving strategic planning and meticulous execution. To begin with, organizations must perform a comprehensive assessment of their current security environment. This process involves identifying potential vulnerabilities and recognizing areas that require enhanced protection. It is through this evaluation that organizations can prioritize specific aspects of security requiring immediate attention.
Once potential vulnerabilities are identified, the next step in developing enterprise-wide security protocol standards involves collaboration across various departments. Cross-functional teams consisting of IT, compliance, and operations professionals must work together to draft policies that meet both organizational objectives and industry standards. By incorporating insights from different areas, these standards can be realistic, practical, and easily adoptable across the enterprise.
Read Now : Cost-effective Video Cards For Gamers
Evaluating the Impact of Enterprise-Wide Security Protocol Standards
Understanding the impact of implementing enterprise-wide security protocol standards involves an ongoing process of evaluation and adaptation. Regular assessments enable organizations to review the effectiveness of the implemented standards and identify any gaps. Adapting and updating these protocols in line with evolving threats is essential for maintaining an effective security posture over time.
Establishing a culture that prioritizes security awareness at all organizational levels is another significant impact of these standards. Employees who are well-informed about security threats are more likely to abide by prescribed standards, actively contributing to safeguarding enterprise data. Thus, regular training and communication about the importance of security protocol standards are crucial for sustaining organizational security.
Challenges in Implementing Enterprise-Wide Security Protocol Standards
One of the primary challenges in implementing enterprise-wide security protocol standards is achieving buy-in from stakeholders across the organization. Convincing all departments about the necessity and benefits of uniform security protocols might require dedicated advocacy and communication from leadership. Additionally, aligning these standards with existing processes without disrupting business operations can be demanding.
Integrating enterprise-wide security protocol standards with existing technology infrastructure also poses challenges. Organizations must ensure that security protocols are compatible with the current systems to avoid operational inefficiencies. Lastly, the dynamic nature of cyber threats necessitates continuous updates and enhancements of security protocols, requiring resources and commitment from the organization.
Role of Technology in Enterprise-Wide Security Protocol Standards
Technology plays a pivotal role in the effective implementation of enterprise-wide security protocol standards. Utilizing advanced encryption tools and security software safeguards data against unauthorized access, providing a technical backbone to these protocols. Moreover, automated security solutions facilitate continuous monitoring and alerting, enabling swift responses to threats before they cause significant harm.
Integrating technology into security protocols also aids in compliance with regulatory requirements by ensuring that all data transactions and security measures are meticulously recorded and easily accessible for audits. As organizations continue to rely on technological advancements, maintaining up-to-date security infrastructure becomes paramount for sustaining enterprise-wide security protocol standards.
Summary of Enterprise-Wide Security Protocol Standards
In conclusion, establishing enterprise-wide security protocol standards is fundamental to the safeguarding of organizational data and assets. These standards ensure uniform protection across all levels of the organization, aligning security measures with operational goals and compliance requirements. The deployment of comprehensive security standards not only mitigates risk but also enhances organizational integrity and trust among clients and stakeholders.
However, the journey towards implementing effective enterprise-wide security protocol standards is not without challenges. Organizations must negotiate stakeholder engagement, technology integration, and evolving security threats. Nonetheless, with strategic planning, cross-functional collaboration, and a commitment to continuous improvement, these challenges are surmountable, paving the way for a secure enterprise environment.