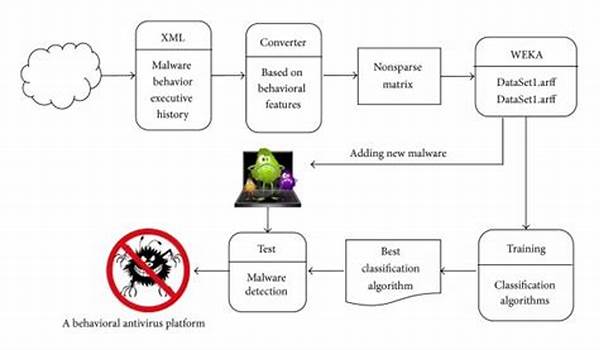
In today’s digital landscape, the protection of systems and data is paramount. Malware, malicious software designed to harm or exploit systems, continues to evolve in complexity and sophistication. Traditional methods of malware detection often fall short in identifying these evolving threats. This is where behavioral analysis steps in as a powerful tool in cybersecurity. By observing the behavior of applications and systems, this method offers a dynamic approach to malware detection. Understanding how threats behave allows security professionals to identify and mitigate risks more effectively, ensuring the integrity of digital environments.
Read Now : Understanding Refurbished Computer Warranty Terms
Understanding Behavioral Analysis in Malware Detection
Malware detection using behavioral analysis involves observing the actions of a program in a controlled environment. Unlike traditional methods that rely on signature-based detection, behavioral analysis does not require previous knowledge of the malware. Instead, it focuses on identifying suspicious activities indicative of malicious intent. For instance, if an application unexpectedly attempts to access sensitive files or network resources, it may be flagged for further investigation.
This method’s strength lies in its ability to adapt to new threats. By studying the behavior patterns of malware, security systems can detect and respond to threats in real time. This proactive approach not only helps in identifying known types of malware but also in discovering zero-day attacks that lack established signatures. As cyber threats become increasingly sophisticated, the use of behavioral analysis in malware detection is becoming essential for organizations to maintain their cybersecurity posture.
Key Processes in Behavioral Analysis
1. Monitoring System Behavior: Constant monitoring of system activities is crucial. Malware detection using behavioral analysis involves scrutinizing actions such as unauthorized file manipulation and unusual network traffic, which helps identify potential threats early.
2. Anomaly Detection: The core of behavioral analysis is identifying anomalies. By establishing a baseline of normal behavior, deviations can signal possible malicious activities, allowing for timely intervention and threat neutralization.
3. Sandboxing: Running suspicious applications in a controlled setting allows security systems to observe behaviors without risking critical systems. This step is vital in malware detection using behavioral analysis as it provides valuable insight into malicious intent.
4. Heuristic Analysis: This process involves examining the behavior of new threats to recognize malware families. By identifying patterns and similarities in action, heuristic analysis strengthens the detection of previously unknown malware.
5. Integrating Machine Learning: Machine learning enhances malware detection using behavioral analysis by enabling systems to learn from past behaviors and improve future detection capabilities. Such integration is vital for keeping pace with evolving cyber threats.
Challenges in Implementing Behavioral Analysis
While malware detection using behavioral analysis presents significant advantages, it also comes with its challenges. One notable challenge is the potential for false positives. Since this method relies heavily on identifying unusual behavior, legitimate applications may sometimes be flagged as malicious, leading to unnecessary alerts and interventions.
Moreover, setting up an effective behavioral analysis framework requires considerable resources and expertise. Continuous monitoring, analysis, and updates to the system are necessary to keep it functional and relevant to emerging threats. Despite these challenges, the benefits of a proactive and dynamic approach to detecting malware far outweigh the limitations, making it a critical component of modern cybersecurity strategies.
Techniques to Enhance Behavioral Analysis
1. Advanced Machine Learning Algorithms: Utilizing sophisticated machine learning algorithms can improve the accuracy of malware detection using behavioral analysis by refining the detection and prediction models.
2. Integration with Threat Intelligence: Combining behavioral analysis with global threat intelligence data enables a broader perspective on threat patterns and enhances the detection process.
3. User Behavior Analytics: Incorporating user behavior analytics provides additional context and helps in distinguishing between normal and potentially malicious activities within a system.
4. Automated Response Protocols: Developing automated response mechanisms ensures prompt action against identified threats, thus minimizing potential damage through timely intervention.
Read Now : Differences In Warranty Terms Explained
5. Regular System Audits: Conducting regular system audits helps maintain the integrity of the behavioral analysis framework by revealing areas that require improvement or adjustment.
6. Cross-Platform Compatibility: Ensuring that behavioral analysis techniques are applicable across different platforms and environments strengthens the overall cybersecurity posture of an organization.
7. Comprehensive Logging and Reporting: Detailed logging and reporting facilitate a better understanding of detected threats and support continuous improvement of the analysis framework.
8. Human Expertise Collaboration: Leveraging human expertise in conjunction with automated systems provides a balanced and effective approach to malware detection using behavioral analysis.
9. Real-Time Analysis: Implementing real-time analysis capabilities allows for immediate action against threats and reduces the window of opportunity for malicious activities.
10. Behavioral Baseline Establishment: Creating a detailed baseline of normal system behavior is imperative for accurately identifying anomalies during the analysis process.
Future of Malware Detection Using Behavioral Analysis
The future of malware detection using behavioral analysis looks promising. As cyber threats continue to evolve, the need for adaptive and robust detection systems increases. With the integration of advanced technologies like artificial intelligence and machine learning, behavioral analysis is set to become even more precise and efficient in identifying threats.
Organizations are progressively realizing the importance of investing in innovative detection methodologies. As these methods mature, the distinction between legitimate and malicious activities will become clearer, minimizing false positives and increasing detection rates. The continued evolution of this field is critical as it aligns with the ever-changing landscape of cyber threats, ensuring that organizations remain one step ahead.
Summary
In summary, malware detection using behavioral analysis offers a comprehensive and adaptive approach to cybersecurity. By focusing on the behavior of applications rather than their signatures, this method addresses the limitations of traditional detection systems. While challenges such as false positives and resource demands exist, the benefits far overshadow these limitations.
The incorporation of cutting-edge technologies, such as machine learning and AI, enhances the capacity of behavioral analysis frameworks, promising a more secure digital future. As cyber threats evolve, the need for dynamic and proactive security measures becomes crucial. Consequently, malware detection using behavioral analysis is not just a trend but a necessity for any organization prioritizing its digital security. By embracing these advancements, security professionals are better equipped to navigate the complex landscape of cybersecurity threats.