In today’s rapidly evolving digital landscape, securing sensitive information and protecting infrastructure is paramount. As threats become more sophisticated, organizations must prioritize identifying and evaluating security risks. This ensures vulnerabilities are addressed before they can be exploited by malicious actors. This article explores various approaches and methodologies that are essential for crafting robust security strategies.
Read Now : Scalability In Data Infrastructure
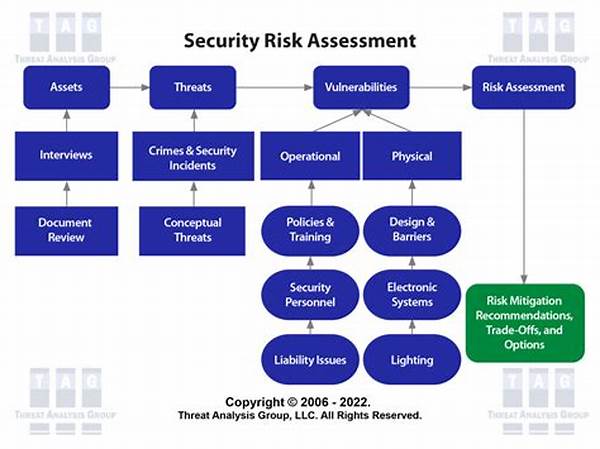
Understanding the Importance of Security Risk Evaluation
The task of identifying and evaluating security risks cannot be understated. As organizations grow, they inadvertently expand their attack surface, making them more susceptible to cyber threats. Understanding the potential risks allows for better preparation and implementation of protective measures. This process begins with a thorough asset inventory, identifying what needs protection and which threats are most likely to impact these assets.
Once vulnerabilities are identified, it’s crucial to assess the likelihood and impact of these threats. This evaluation involves a combination of qualitative and quantitative analyses. For example, considering the severity of a data breach and the cost of mitigation measures. By understanding these dynamics, businesses can shape their security protocols to mitigate risks appropriately.
Ultimately, security risk evaluation guides organizations in aligning their security strategies with their overall business goals. This ensures resources are allocated efficiently, maximizing protection while minimizing overspending. In a world where security breaches can spell disaster, maintaining vigilance through identifying and evaluating security risks is an essential component of any business strategy.
Key Elements in Identifying and Evaluating Security Risks
Strategies for Effective Risk Management
Identifying and evaluating security risks is no simple task and requires a multifaceted approach. Organizations must first establish a strong security culture among employees. Training programs and awareness campaigns are vital, as human error often presents substantial risks. By fostering a culture that prioritizes security, organizations can reduce vulnerabilities significantly.
Another crucial strategy involves leveraging technology to enhance security measures. This includes deploying advanced tools such as intrusion detection systems, firewalls, and encryption. These technologies aid in the continuous monitoring of networks, ensuring real-time threat detection and response. When identifying and evaluating security risks, technology becomes an invaluable ally in maintaining a robust defense posture.
Additionally, collaboration with external partners, like cybersecurity consultants, can provide fresh perspectives on risk assessment. These partnerships ensure organizations benefit from the latest industry insights and technologies, further enhancing their ability to identify and evaluate security risks effectively. By adopting these strategies, businesses can navigate the complex landscape of modern threats with greater confidence.
Enhancing Risk Evaluation Processes
Developing comprehensive procedures for identifying and evaluating security risks requires a strategic framework. The following components are essential:
1. Continuous Monitoring: Implement systems that provide ongoing surveillance of networks and infrastructures to quickly identify and evaluate any emerging security risks.
2. Regular Audits: Frequent audits help in understanding the current security posture and uncovering potential vulnerabilities that might have arisen since the last evaluation.
3. Policy Updates: Keeping security policies current with emerging threats ensures organizations are consistently protecting against the latest risks while identifying and evaluating security risks.
4. Stakeholder Engagement: Involving all relevant stakeholders in the security risk identification process ensures a more comprehensive understanding of potential threats.
5. Data Encryption: Protecting sensitive data through encryption reduces the impact of data breaches, an integral step in evaluating security risks.
6. Simulation Exercises: Conducting drills and simulations aids in preparing for potential cyber threats, highlighting areas needing improvement.
7. Threat Intelligence: Utilizing threat intelligence feeds can provide insights into current cyber threat trends, aiding in the accurate identification of security risks.
Read Now : Preventing Computer System Crashes
8. Compliance Checks: Regular compliance checks ensure adherence to industry standards, aiding in the identification and evaluation of where the organization stands in its security measures.
9. Network Segmentation: By dividing network environments, organizations can create containment zones, reducing the spread of potential threats.
10. Incident Reviews: Post-incident analyses provide lessons learned, aiding in preventing similar events and improving future risk evaluations.
From Evaluation to Implementation: Applying Risk Assessments
The journey from identifying and evaluating security risks to implementing mitigation strategies is crucial for organizational resilience. Once risks have been identified and assessed, the next step is prioritizing them based on potential impact and likelihood. This prioritization allows for the allocation of resources towards the most pressing vulnerabilities, balancing security and cost efficiency.
Implementing solutions involves integrating both technical controls and organizational strategies. Technical measures such as firewalls, antivirus software, and patch management systems are vital in protecting against a wide array of threats. Meanwhile, organizational measures, including employee training and policy development, play an equally vital role in fortifying security. Both components are intertwined, creating a comprehensive defense against potential risks.
Effective communication is essential throughout this process. Ensuring all members within the organization are aware of new protocols and understand their role in risk mitigation is key to successful implementation. Regular updates and training sessions keep the workforce informed and engaged, further strengthening the organization’s security posture. Ultimately, through a methodical and inclusive approach, organizations can transform risk assessments into actionable strategies, reducing vulnerability and enhancing overall security resilience.
Fostering a Proactive Security Culture
In cultivating a security-conscious environment, identifying and evaluating security risks must become a collaborative effort. Encouraging employee involvement in security measures fosters a sense of ownership and accountability. Training programs tailored to different roles within the organization ensure that risks are understood across all levels, making security a shared responsibility.
Regular workshops and seminars addressing current security trends can keep employees informed and motivated to remain vigilant. By making security awareness an integral part of organizational culture, employees can more effectively contribute to identifying and evaluating security risks, spotting potential vulnerabilities quickly, and suggesting improvements to existing measures.
Open lines of communication are paramount. Channels for reporting potential security concerns should be accessible and anonymous if need be, enabling employees to report suspicious activities without fear. Ultimately, fostering a proactive security culture enables organizations to stay ahead of emerging threats, ensuring that identifying and evaluating security risks remains a core component of the organizational strategy.
Summary: Cultivating a Resilient Security Framework
The landscape of cybersecurity is ever-evolving, making the process of identifying and evaluating security risks a perpetual necessity. By leveraging a combination of technology, strategy, and human insight, organizations can develop robust defenses against potential threats. The goal is to transform mere identification into actionable insights that empower businesses to adapt and fortify their security posture continuously.
At the heart of a resilient security framework lies an informed and engaged workforce. Empowering employees with the knowledge and tools to identify risks ensures a swift and unified response. Paired with cutting-edge technologies and strategic partnerships, this creates an environment where security risks are not just managed but anticipated and neutralized proactively.
By embedding these robust identification and evaluation practices into the organizational fabric, companies bolster their defenses and ensure a proactive stance against threats. In an era where security challenges are increasingly complex, maintaining this vigilance is crucial in safeguarding not only data but the trust and confidence of stakeholders and clients alike.